Plateforme
La manière la plus efficace de gérer l’IT
Simplifiez le travail des administrateurs IT grâce à des workflows personnalisés, des autorisations et politiques dynamiques et des rapports détaillés sur les utilisateurs et les appareils.
En cliquant sur « Découvrir Rippling », vous acceptez que vos données soient utilisées conformément à l’Avis de confidentialité de Rippling, y compris à des fins commerciales.
DEMANDES D’EXTRACTION
Service
Emplacement

Certifications de conformité

Situation d’emploi
Vérification des antécédents

DEMANDES D’EXTRACTION
Service
Emplacement

Certifications de conformité

Situation d’emploi
Vérification des antécédents

DEMANDES D’EXTRACTION
Service
Emplacement

Certifications de conformité

Situation d’emploi
Vérification des antécédents

Statut MDM
Type de processeur
Incident Jira
MANAGER

Commande d’appareils
Menaces détectées

Fabricant

État du chiffrement
Statut MDM
Type de processeur
Incident Jira
MANAGER

Commande d’appareils
Menaces détectées

Fabricant

État du chiffrement
Statut MDM
Type de processeur
Incident Jira
MANAGER

Commande d’appareils
Menaces détectées

Fabricant

État du chiffrement
NIVEAU
Année du modèle

SUBORDONNÉS DIRECTS
NOM

Taille de l’écran
Système d’exploitation
ÉTAT DE LA BATTERIE
NIVEAU

Date d’achat
SUBORDONNÉS DIRECTS
NIVEAU
Année du modèle

SUBORDONNÉS DIRECTS
NOM

Taille de l’écran
Système d’exploitation
ÉTAT DE LA BATTERIE
NIVEAU

Date d’achat
SUBORDONNÉS DIRECTS
NIVEAU
Année du modèle

SUBORDONNÉS DIRECTS
NOM

Taille de l’écran
Système d’exploitation
ÉTAT DE LA BATTERIE
NIVEAU

Date d’achat
SUBORDONNÉS DIRECTS
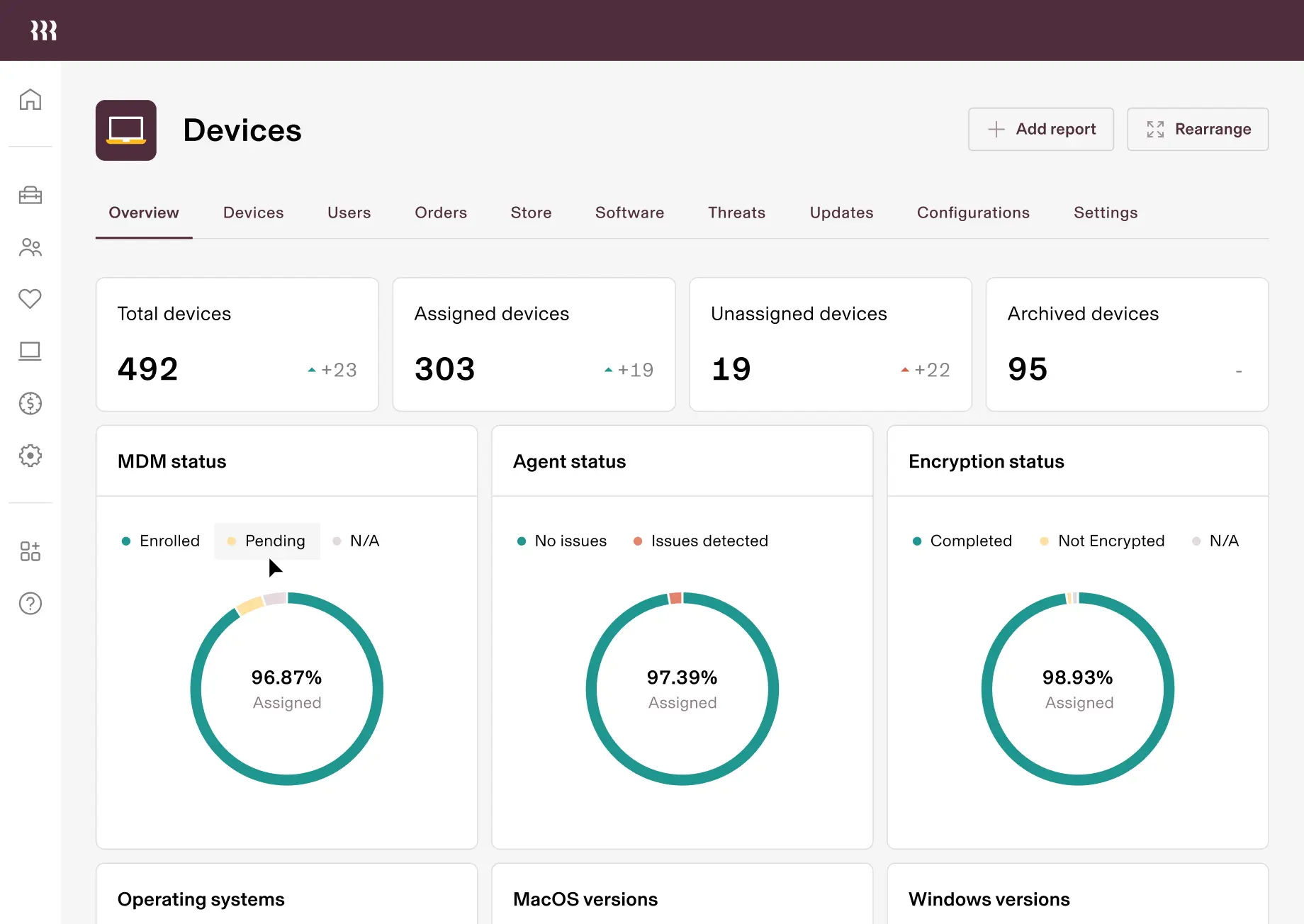
Basé sur une source unique de vérité
Unifiez votre fournisseur d’identité et votre SIRH sur un ensemble de données universel pour tirer parti de centaines d’attributs d’utilisateurs et d’appareils, sans qu’il soit nécessaire de rapprocher manuellement les données ou de créer des intégrations.
Capacités de la plateforme
Tous les outils dont vous avez besoin pour gérer l’IT
Utilisez des centaines d’attributs dans le répertoire des utilisateurs pour créer et personnaliser en quelques clics des workflows, des politiques, des rapports et plus encore.
Workflows simplifiés
Automatisez un maximum de processus, des tâches simples d’onboarding aux alertes de sécurité avancées grâce à des workflows personnalisés, et améliorez l’efficacité de chacun des aspects de votre fonction IT.
Détectez toute activité suspecte


Maîtrisez les retards de commande


Surveillez l’activité des appareils


Politiques basées sur les rôles
Utilisez des groupes dynamiques d’utilisateurs et d’appareils pour appliquer de manière cohérente des contrôles d'accès, des exigences de sécurité et d’autres règles basées sur les rôles.
Automatisez le provisionnement de compte


Appliquez différentes politiques d’authentification multifacteur selon le rôle


Déployez des politiques multicouches de confiance dans les appareils


Gestion des approbations
Définissez des chaînes d’approbation pour les actions prises durant l’onboarding et l’offboarding afin d’automatiser la gestion IT tout au long du cycle de vie de l’utilisateur.
Appliquez des budgets pour les appareils


Gérez les demandes d’accès


Contrôlez les affectations d’appareils


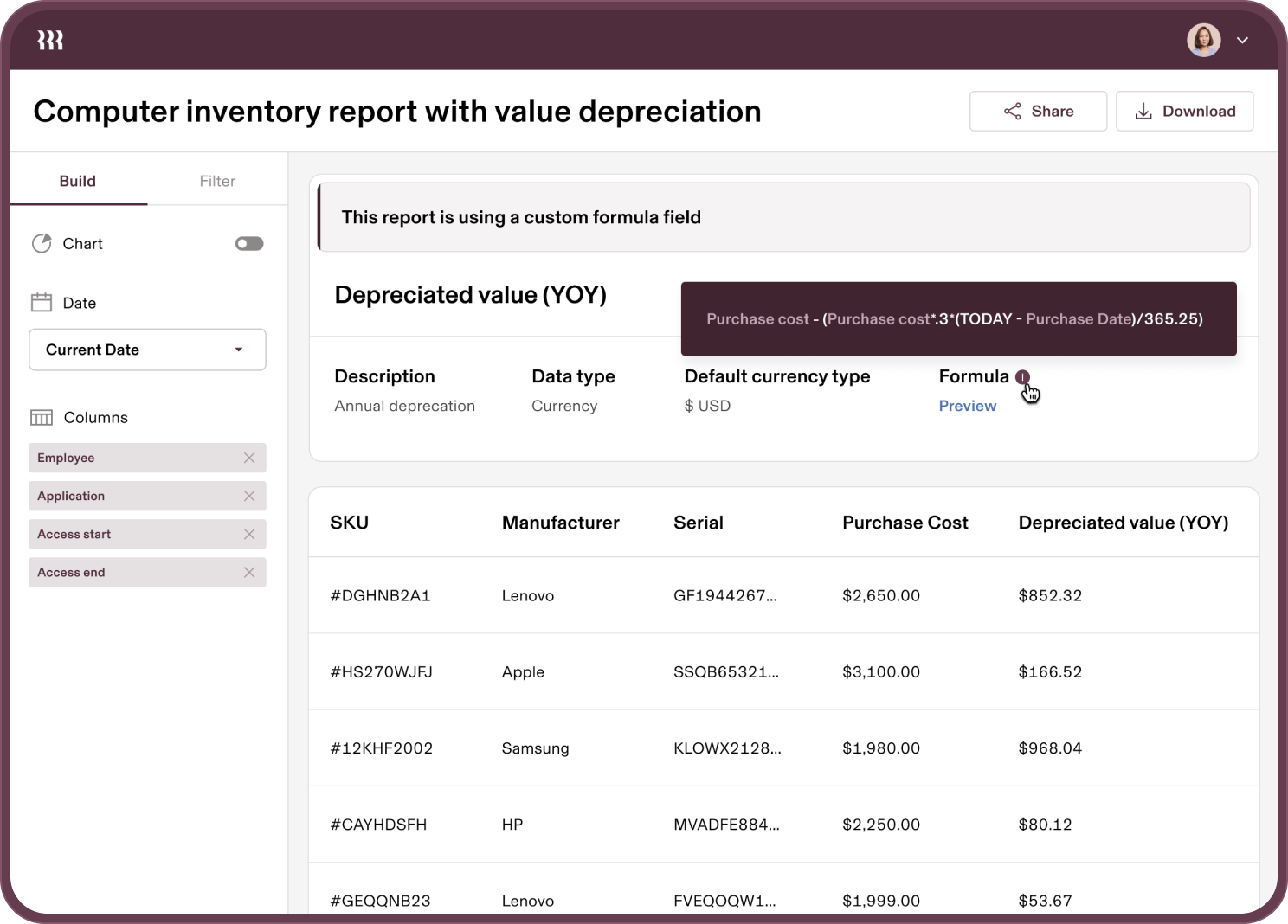
Analytique avancée
Analytique avancée
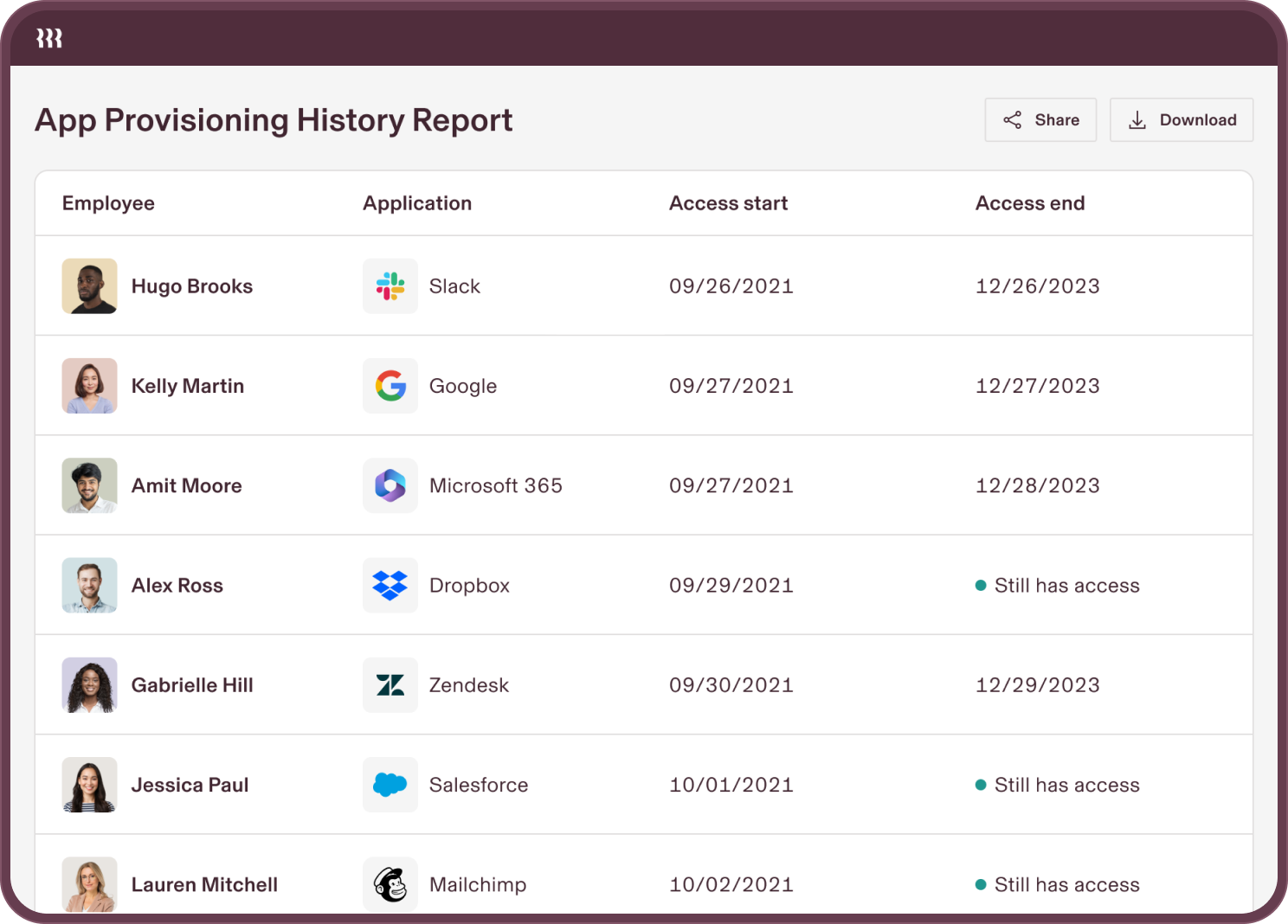
Bénéficiez d’une visibilité complète sur les utilisateurs et les appareils grâce à des rapports personnalisés couvrant tous les aspects, des audits SOC 2 aux coûts des appareils.
Profils d’autorisation précis
Allez au-delà des profils basiques d’administration et de consultation. Accordez à vos utilisateurs le niveau d’accès approprié. Les profils d’autorisation sont automatiquement mis à jour dès l’onboarding du collaborateur et jusqu’à son offboarding, y compris lorsqu’il change de rôle.

Changement de rôle

Les autorisations ont été mises à jour

Nouvelle recrue : Directeur informatique

Le profil d'autorisation a été attribué

L’offboarding du collaborateur est terminé

Toutes les autorisations ont été désactivées



MODÈLES
Tirez rapidement le meilleur parti de Rippling
Grâce aux Modèles, créez exactement les workflows, rapports et autres processus dont vous avez besoin dans Rippling. Nos modèles prédéfinis répondent aux problématiques courantes en matière de sécurité et de conformité.



SOC 2 Type II, ISO 27001, CSA STAR Niveau 2
Rippling combine des fonctionnalités de sécurité de qualité professionnelle à des audits réguliers pour garantir la protection en tout temps de vos données.
En savoir plus sur la sécurité
Voir Rippling IT en action
Découvrez comment gérer en toute sécurité les identités, les accès, les appareils et les stocks depuis une seule plateforme.