Platform
The most efficient way to run IT
Take the effort out of IT admin with custom workflows, dynamic permissions and policies, and advanced reports for every user and device.
By clicking "See Rippling," you agree to the use of your data in accordance with Rippling's Privacy Notice, including for marketing purposes.
PULL REQUESTS
Department
Location

Compliance certifications

Employment status
Background Checks

PULL REQUESTS
Department
Location

Compliance certifications

Employment status
Background Checks

PULL REQUESTS
Department
Location

Compliance certifications

Employment status
Background Checks

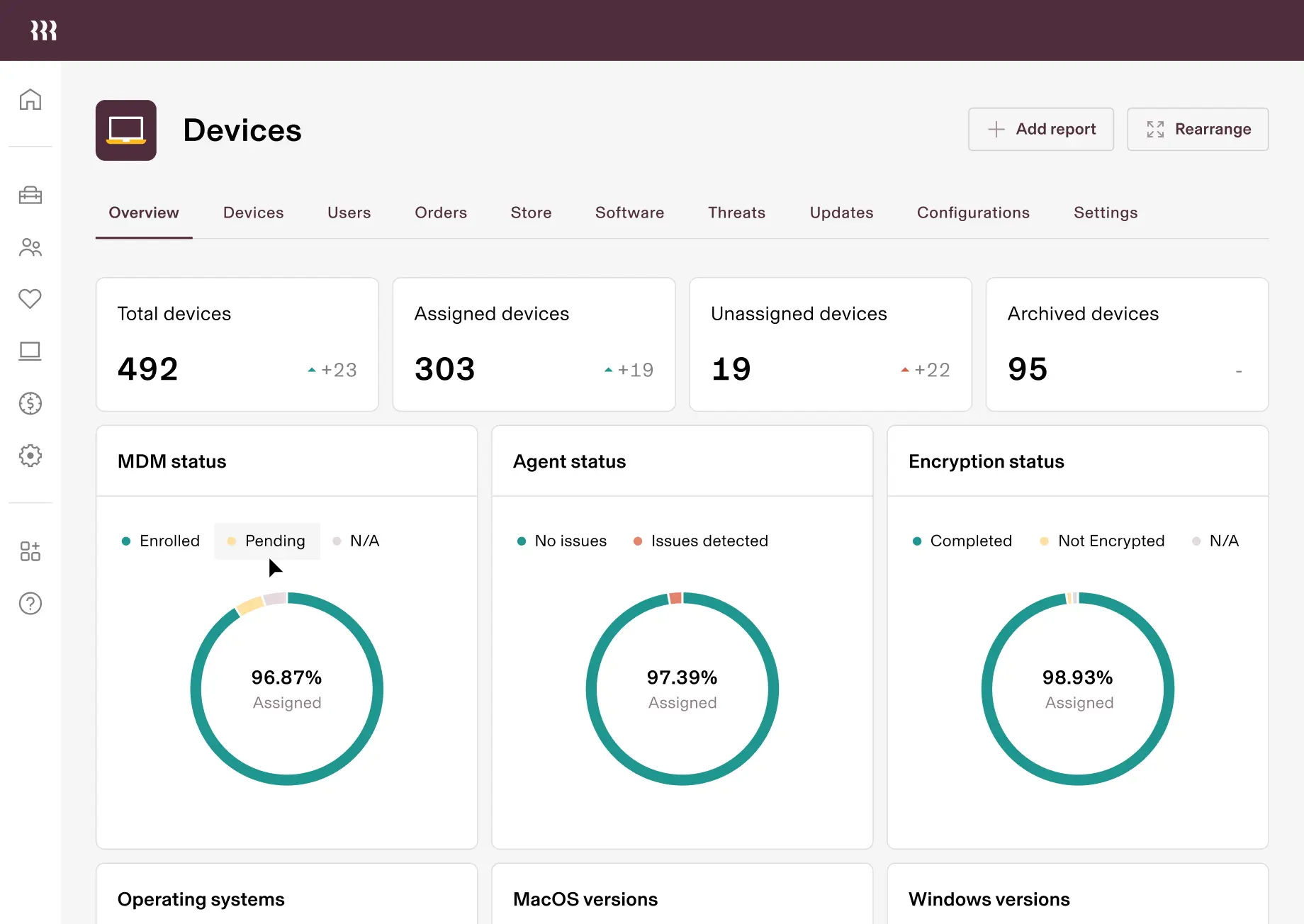
MDM status
CPU Type
Jira issue
MANAGER

Device order
Detected threats

Manufacturer

Encryption Status
MDM status
CPU Type
Jira issue
MANAGER

Device order
Detected threats

Manufacturer

Encryption Status
MDM status
CPU Type
Jira issue
MANAGER

Device order
Detected threats

Manufacturer

Encryption Status
LEVEL
Model year

DIRECT REPORTS
NAME

Screen size
Operating System
BATTERY HEALTH
LEVEL

Purchase date
DIRECT REPORTS
LEVEL
Model year

DIRECT REPORTS
NAME

Screen size
Operating System
BATTERY HEALTH
LEVEL

Purchase date
DIRECT REPORTS
LEVEL
Model year

DIRECT REPORTS
NAME

Screen size
Operating System
BATTERY HEALTH
LEVEL

Purchase date
DIRECT REPORTS
Powered by a single source of truth
Unite your IdP and HRIS on a universal data set to leverage hundreds of user and device attributes—no manual data reconciliation or integration builds needed.
Platform capabilities
All the tools you need to run IT
Leverage hundreds of attributes within the user directory to build custom workflows, policies, reports, and more in just a few clicks.
Streamlined workflows
Automate everything from simple onboarding tasks to advanced security alerts with custom workflows, improving efficiency across every aspect of IT.
Detect suspicious activity


Stay on top of new order delays


Monitor device activity


Role-based policies
Use dynamic groups of users and devices to consistently enforce role-based access controls, security requirements, and more.
Automate account provisioning


Enforce different MFA policies by role


Deploy layered device trust policies


Approval management
Set up approval chains for actions taken during onboarding and offboarding to automate IT management across the user lifecycle.
Enforce device budgets


Manage access requests


Control device assignments


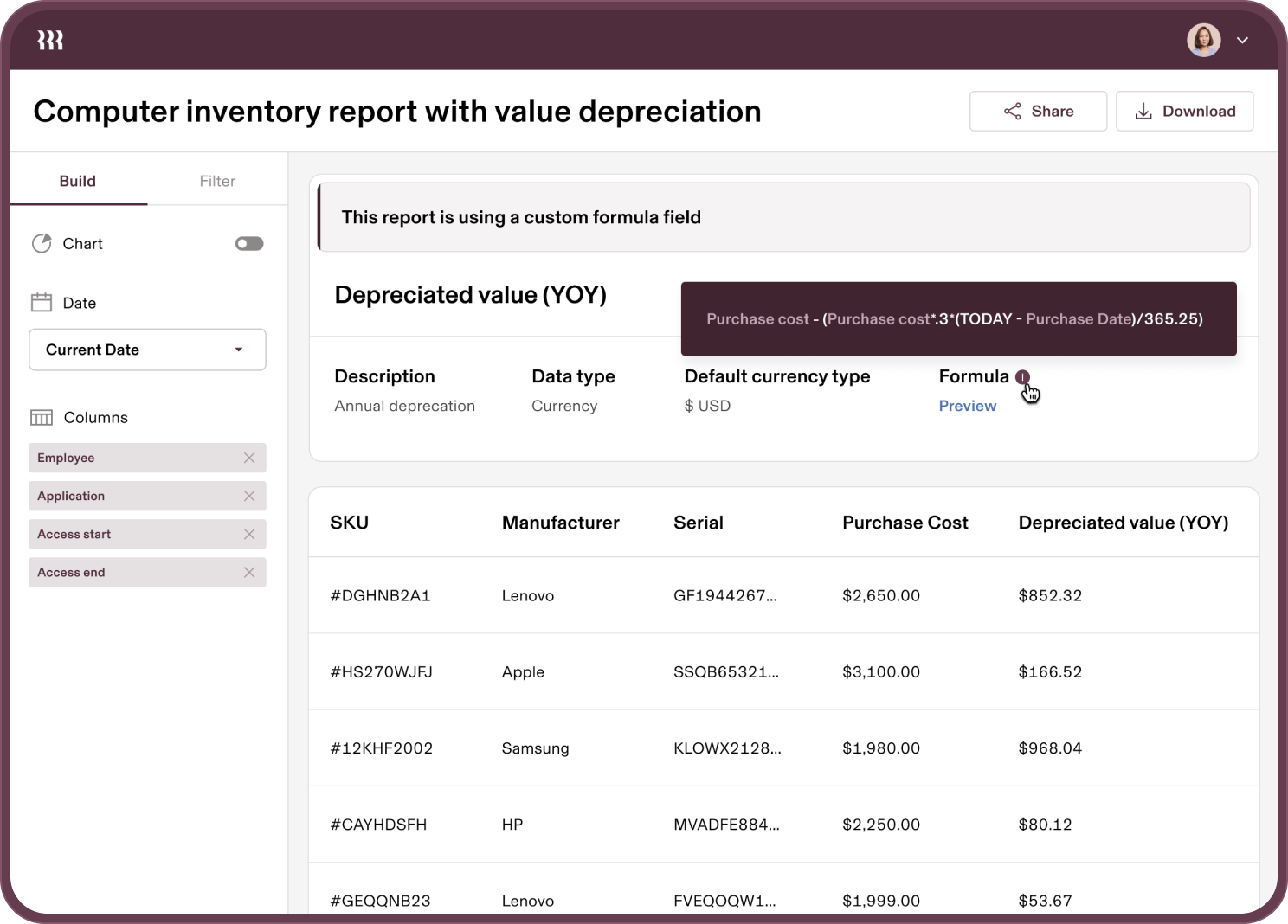
Advanced Analytics
Advanced analytics
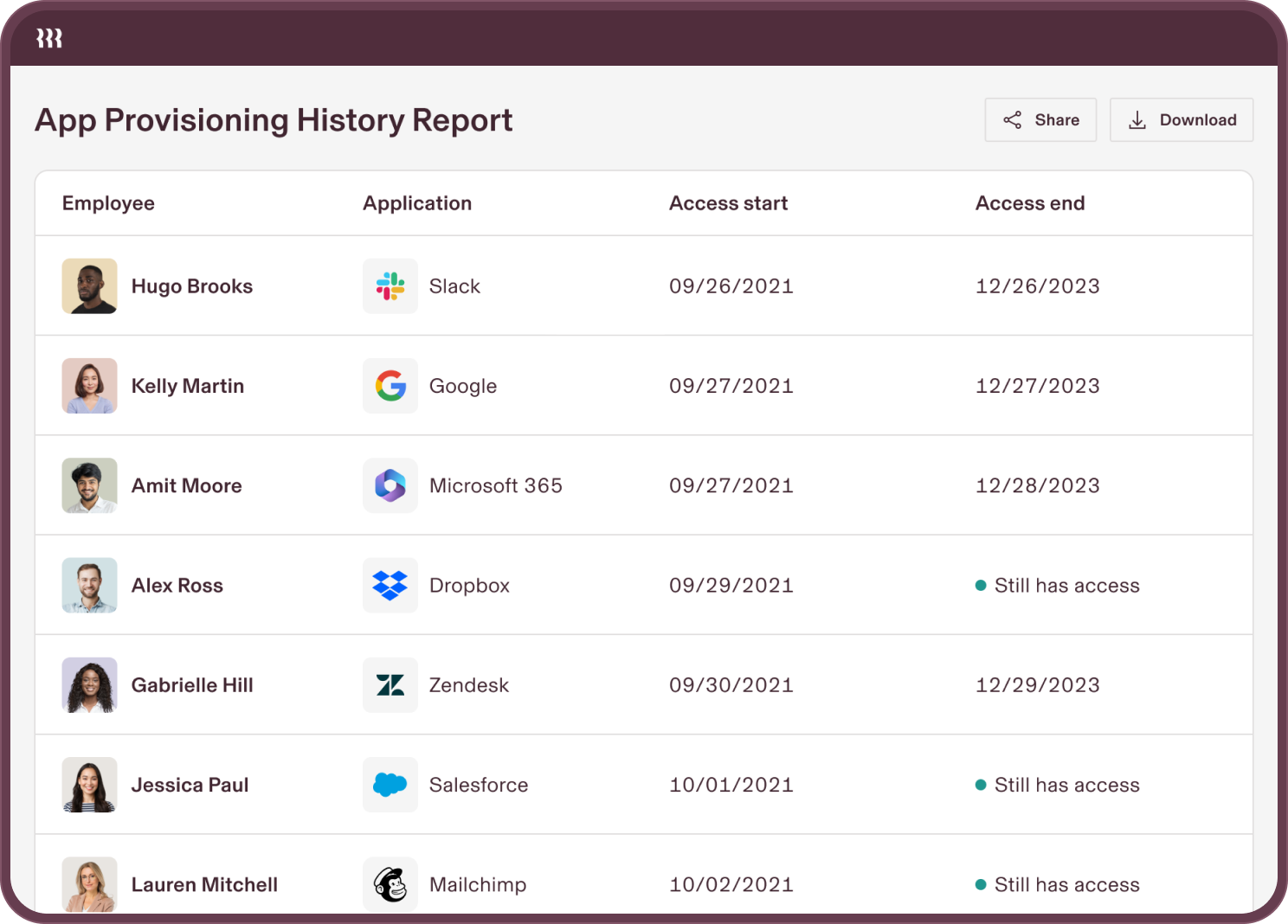
Gain deep visibility into users and devices with custom reports for everything from SOC 2 audits to device costs.
Precise permission profiles
Go beyond basic admin and viewer profiles. Give the right users the right level of access. Permission profiles automatically stay up to date when users onboard, change roles, or offboard.

Role change

Permissions updated

New Hire: Head of IT

Permissions profile assigned

Employee offboarded

Disabled all permissions



RECIPES
Get more out of Rippling faster
Build exactly what you need from Rippling with Recipes—pre-built templates for workflows, reports, and more to solve common security and compliance challenges.



SOC 2 Type II, ISO 27001, CSA STAR Level 2
Rippling combines enterprise-grade security features with regular audits to ensure your data is always protected
Learn more about security
See Rippling IT in action
See how you can securely manage identity, access, devices, and inventory all from one platform.