
Identity and access management software
Get access right,
every time
Rippling combines an HRIS and identity provider (IdP) into one platform – unlocking stronger security with granular access controls across the user lifecycle.











Rippling idp
Single source of truth for user identity
Rippling is the only IAM solution to truly centralise user identity with a unified HRIS and IdP right out-of-the-box – no SCIM integration needed.
PULL REQUESTS
Department
Location

Compliance certifications

Employment status

Background checks

PULL REQUESTS
Department
Location

Compliance certifications

Employment status

Background checks

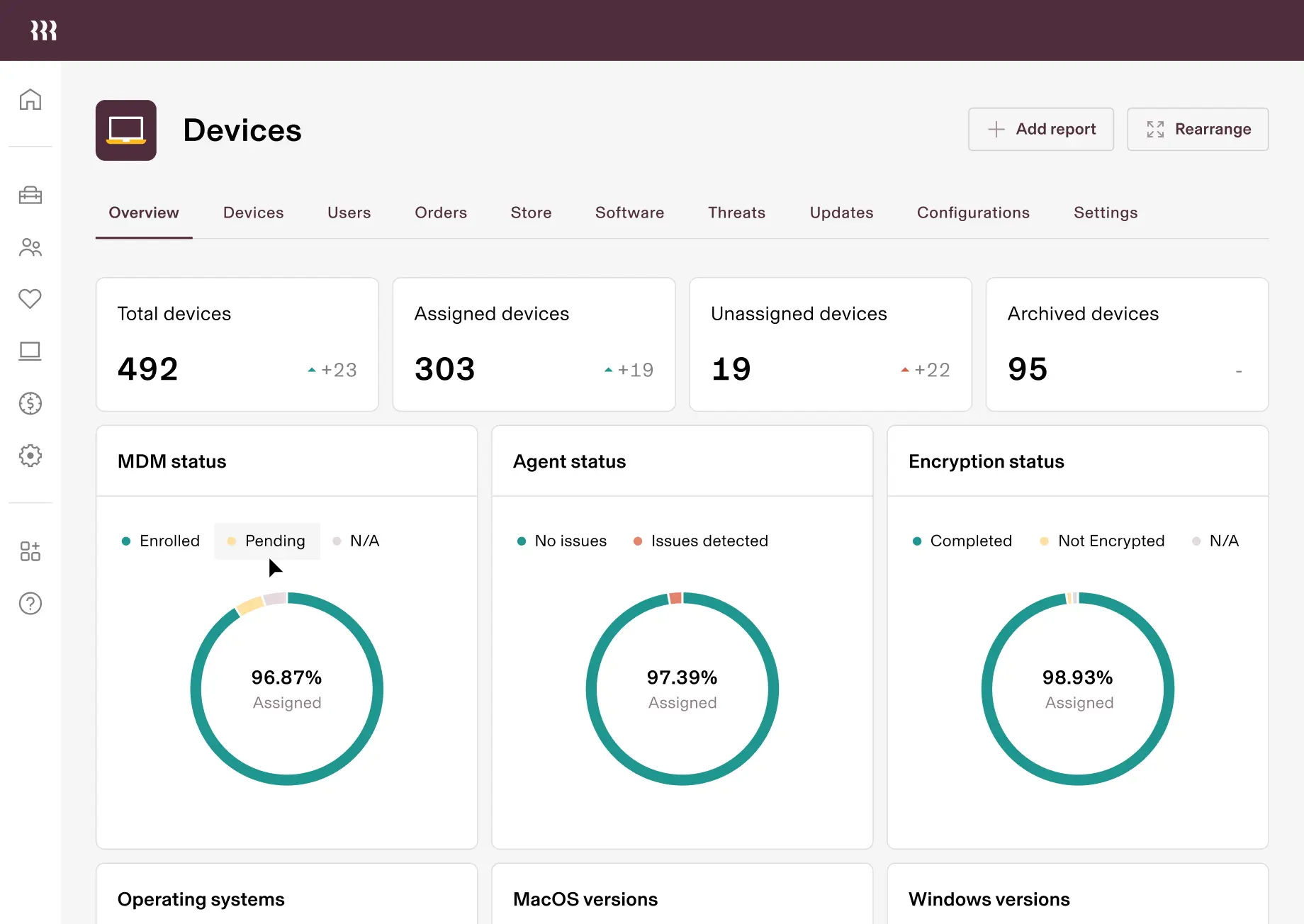
MDM status
CPU type

Jira issue
MANAGER

Device order
Detected threats

Manufacturer

Encryption status
MDM status
CPU type

Jira issue
MANAGER

Device order
Detected threats

Manufacturer

Encryption status
LEVEL
Model year

DIRECT REPORTS
NAME

Screen size

Operating system
BATTERY HEALTH
LEVEL

Purchase date
DIRECT REPORTS
LEVEL
Model year

DIRECT REPORTS
NAME

Screen size

Operating system
BATTERY HEALTH
LEVEL

Purchase date
DIRECT REPORTS
Keep user data in sync
Digital identities are unified across HR, devices and third-party apps, for always accurate and up-to-date user data.
Gain total visibility
Preview and control downstream effects of workforce changes during onboarding, transitions and offboarding.
Customise alerts and automations
Configure workflows and trigger API calls based off of any action or data change inside Rippling or your connected apps.
Airtight access controls
Go beyond standard SCIM attributes. Leverage hundreds of user attributes to create custom zero-trust protocols and ensure nothing slips through the cracks.
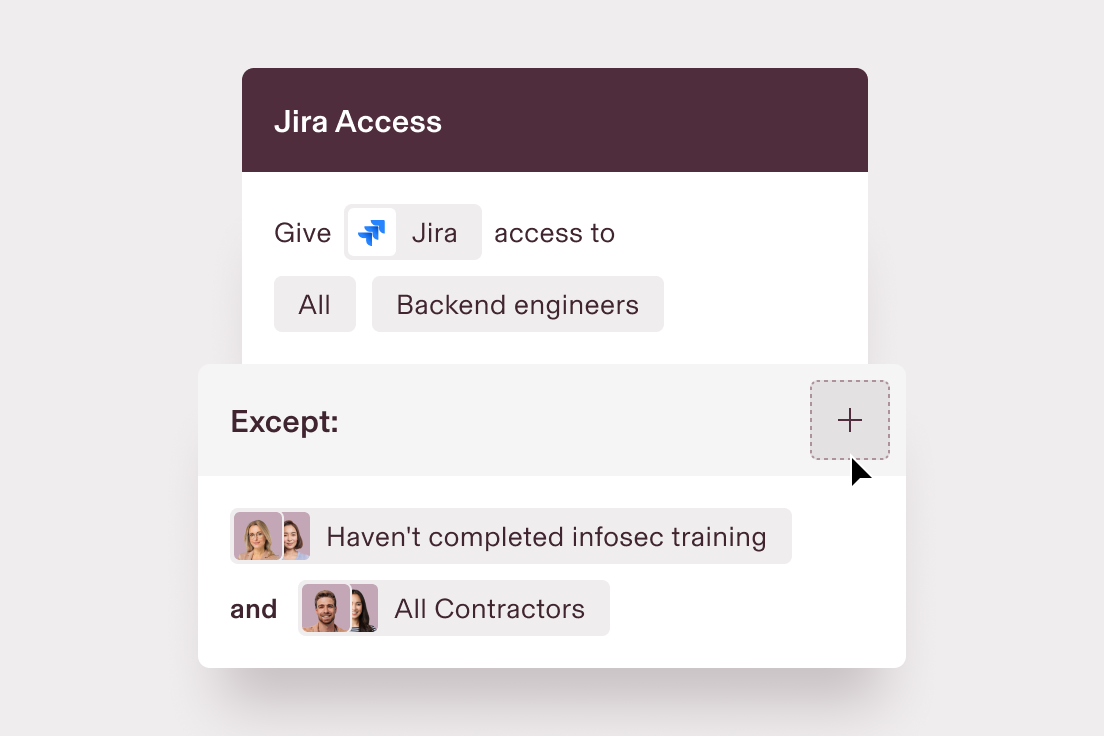
Set dynamic access rules
From provisioning accounts to managing group access, dynamic rules automatically ensure the right people get the right level of access – even as their roles change.

Link identity across systems
Federated identity lets you handle any protocol with ease – from LDAP, Active Directory (AD), OIDC and RADIUS, to custom SCIM and SAML apps.
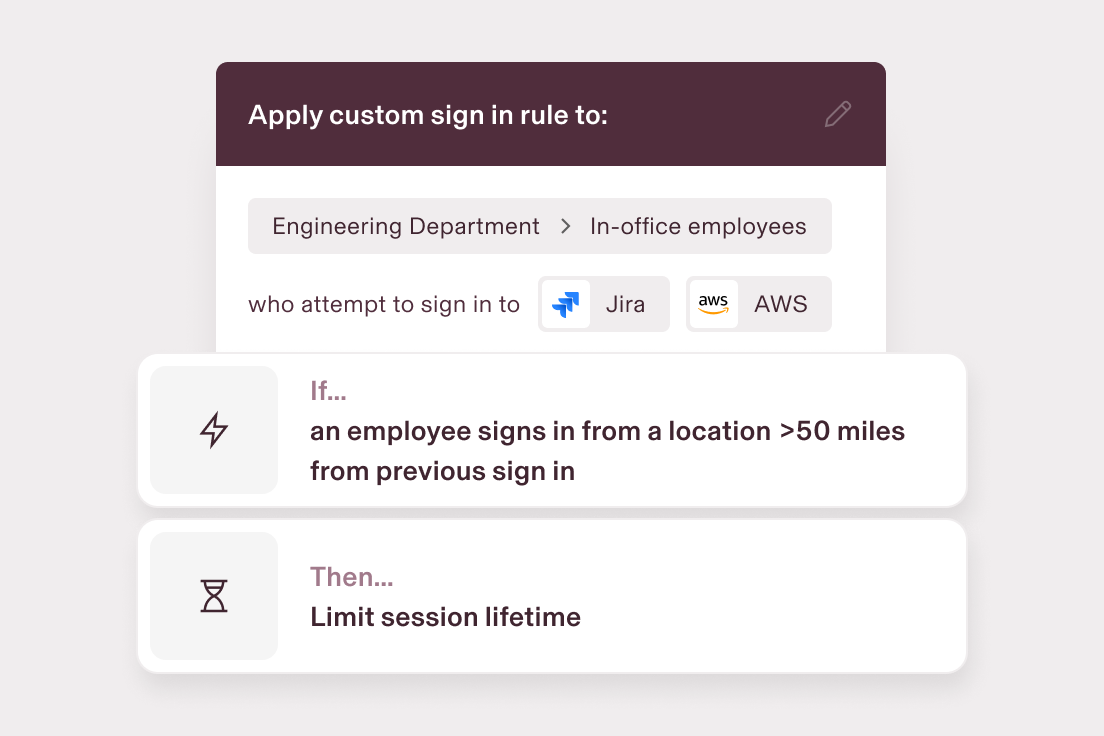
Create behavioural detection rules
Strengthen cybersecurity with dynamic rules based on user roles, departments and behaviours, such as locking users out of your apps automatically after suspicious activity.
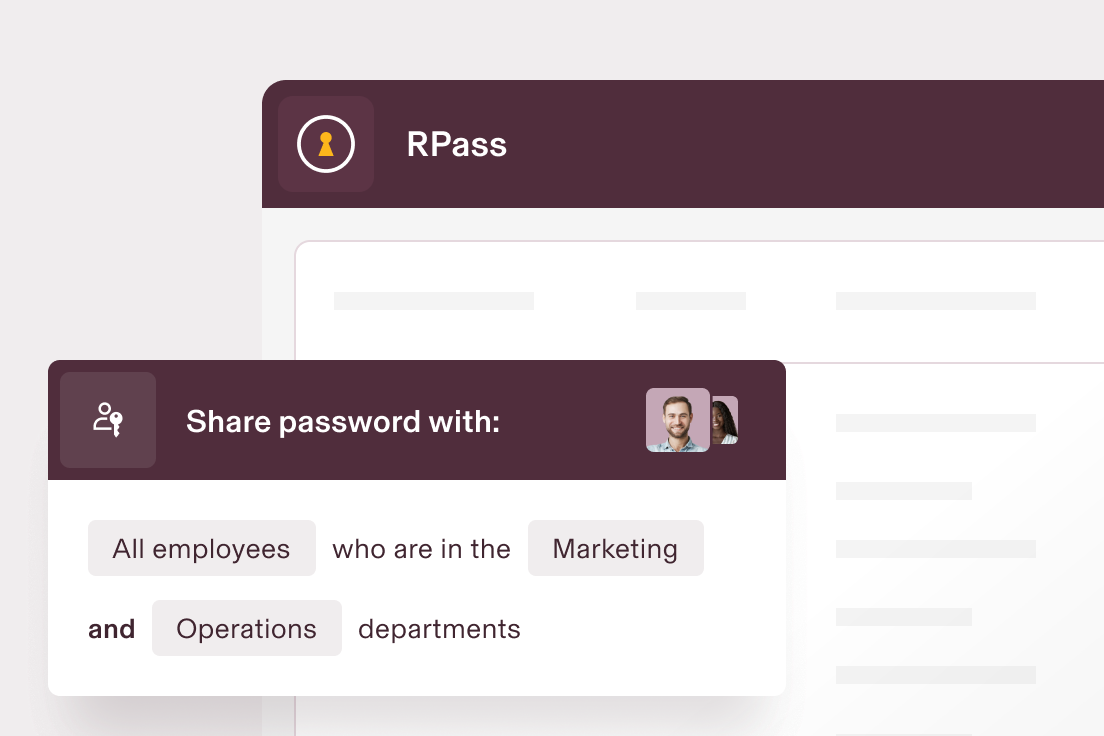
Control password sharing
With our built-in password manager, you’re able to enable user groups to securely store and share passwords in a zero-knowledge vault.
User lifecycle management
Deploy automations across the user lifecycle
Stay in sync with HR and keep access up to date from onboarding to offboarding with custom approval chains, policies and workflows.
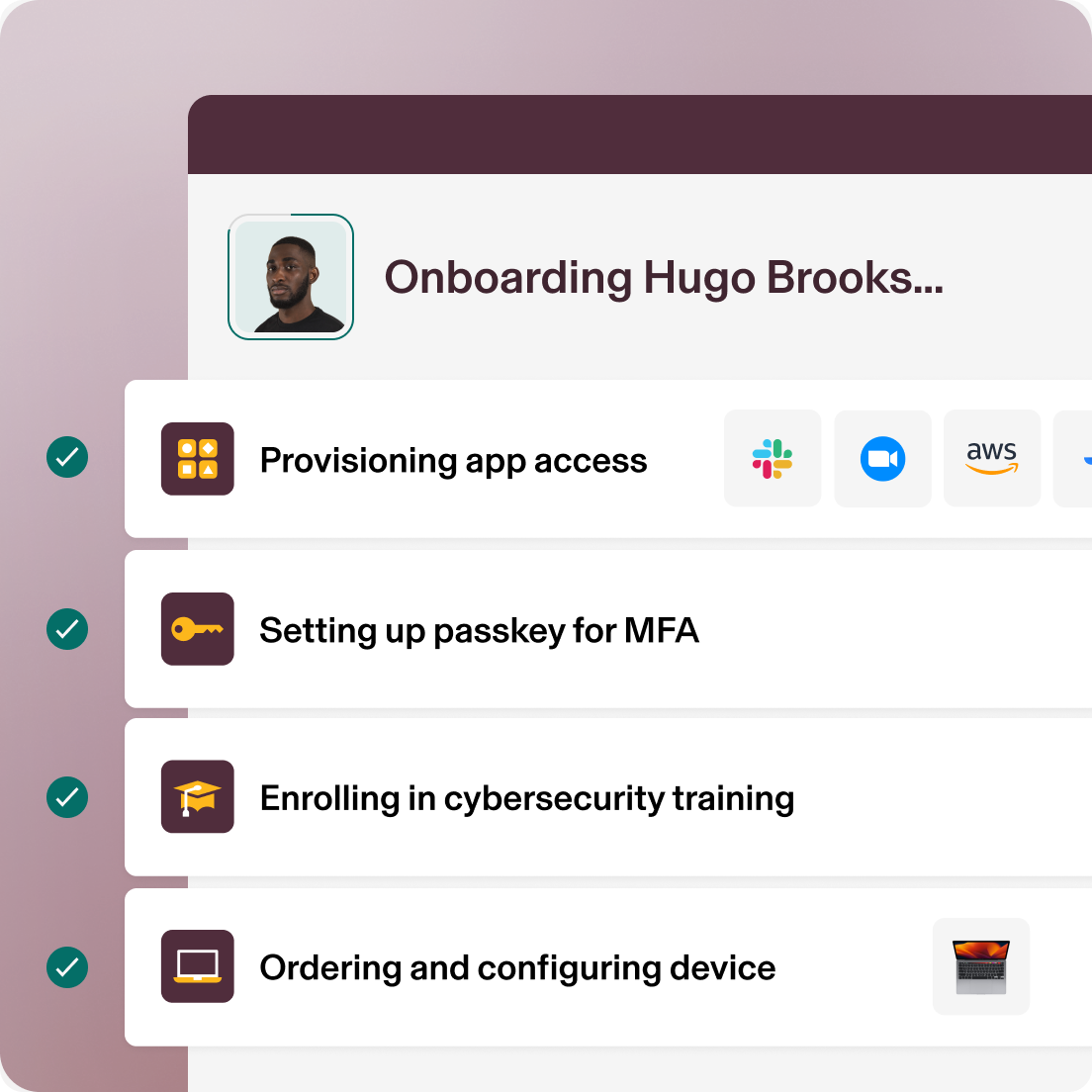
Onboarding

Schedule provisioning, passkeys and third-party group access for new hires down to the minute.
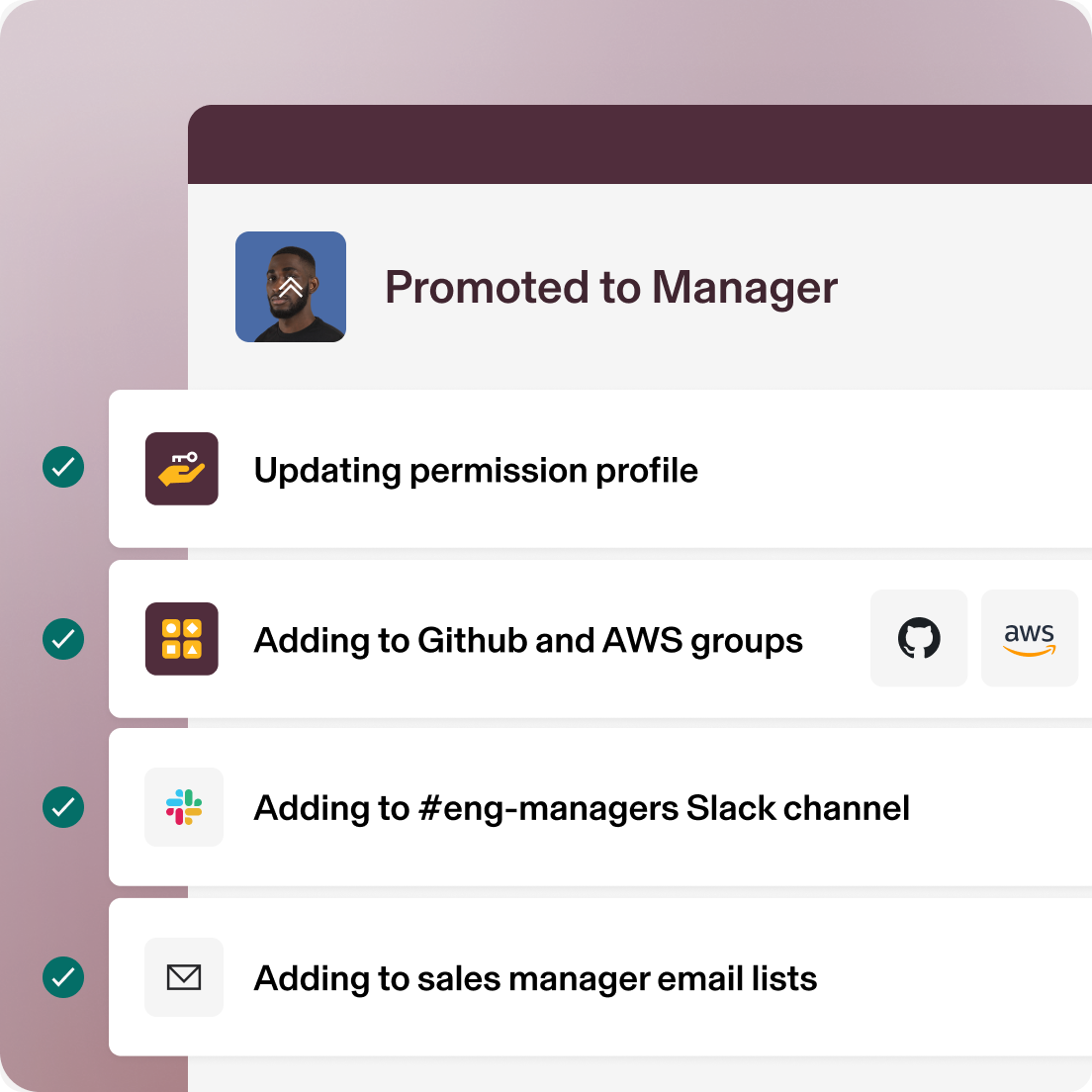
Transitions

Use approval chains and workflows to automate updates to user permissions and group access.
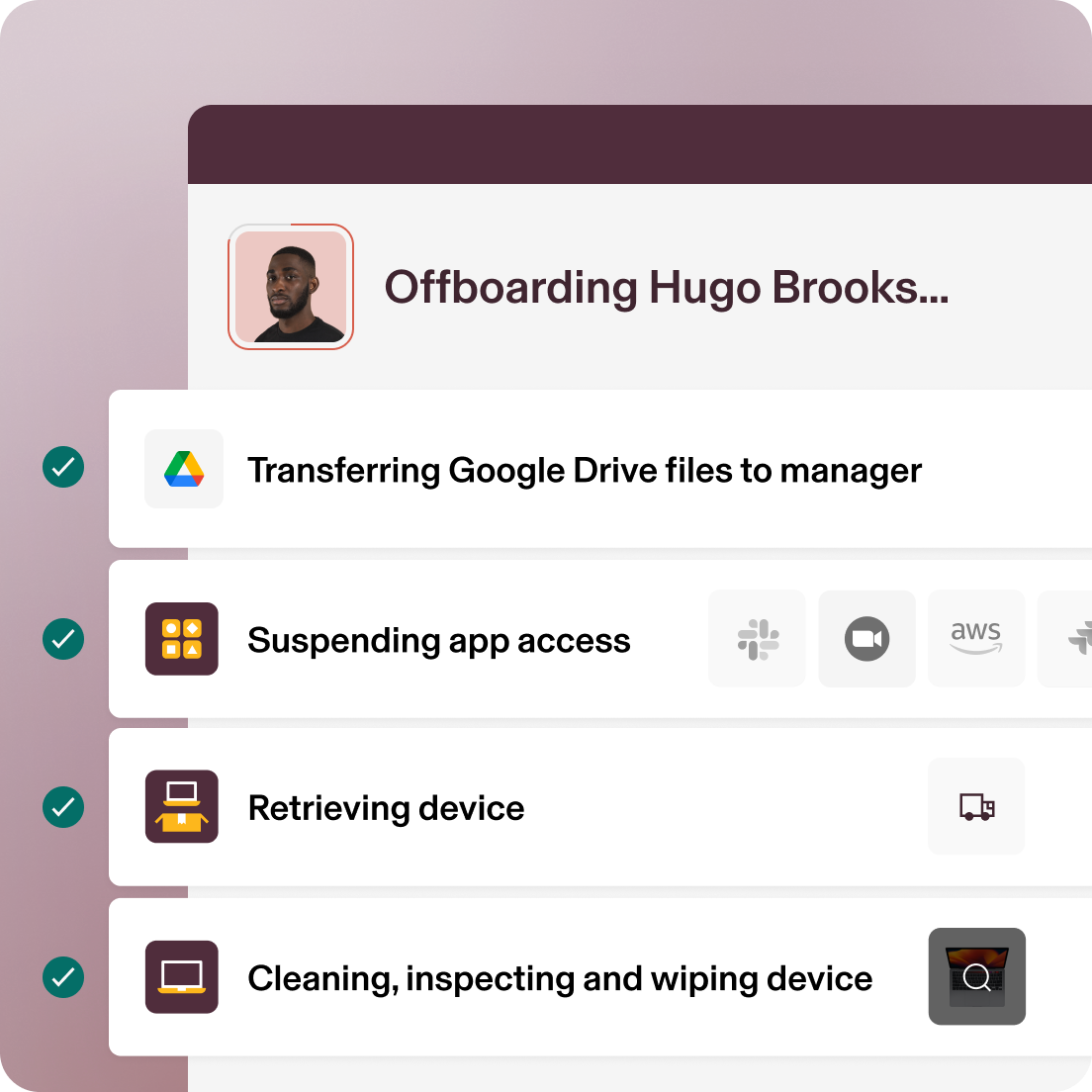
Offboarding

Coordinate with HR and other teams to suspend access, deprovision users and schedule offboarding actions at the right time.
INTEGRATIONS
Level up your tech stack
Integrations don’t just keep your systems in sync. They unlock rich platform capabilities for greater control over your apps and users.
600+ pre-built third-party applications
Custom SCIM integrations
Custom attribute mapping

Slack
Bring team collaboration and communication into one place

Checkr
Run background checks and hire the right candidates faster

Collaborate across Gmail, Drive, Docs, Sheets and more

Zoom
Enable cloud-based video, messaging and meetings

Asana
Effortlessly manage team projects and tasks

Salesforce
Integrated customer relationship management

Microsoft 365
Grant instant access to a suite of premium Microsoft apps

Guideline
Strengthen your retirement benefits with a modern 401(k)

GitHub
Integrate GitHub to automate software development

Carta
Give your people one app to manage all things equity

Jira
Help all types of teams manage resources and deliverables

Datadog
Monitor cloud applications from a single platform

Hubspot
Attract and convert customers with inbound marketing tools

Microsoft Teams
Keep your entire org in sync in one place

Slack
Bring team collaboration and communication into one place

Checkr
Run background checks and hire the right candidates faster

Collaborate across Gmail, Drive, Docs, Sheets and more

Zoom
Enable cloud-based video, messaging and meetings

Asana
Effortlessly manage team projects and tasks

Salesforce
Integrated customer relationship management

Microsoft 365
Grant instant access to a suite of premium Microsoft apps

Guideline
Strengthen your retirement benefits with a modern 401(k)

GitHub
Integrate GitHub to automate software development

Carta
Give your people one app to manage all things equity

Jira
Help all types of teams manage resources and deliverables

Datadog
Monitor cloud applications from a single platform

Hubspot
Attract and convert customers with inbound marketing tools

Microsoft Teams
Keep your entire org in sync in one place
END TO END security
All the security tools you need – and then some

User provisioning

Role-based access controls

Single sign-on (SSO)

Dynamic multi-factor authentication (MFA)

Activity audit logs

Built-in password manager

Compliance reporting

Data attribute mapping
And more
See all


SOC 2 Type II, ISO 27001, CSA STAR Level 2
Rippling combines enterprise-grade security features with regular audits to ensure your data is always protected
Learn more about securityEND-TO-END IT SOFTWARE
Native tools for the entire user and device lifecycle
All
Device management
Identity and access
Inventory management
Built different
Analyse, automate and orchestrate anything
Most "all-in-one" software consists of acquired systems. These modules are disconnected, so your business data is, too. Rippling takes a platform approach, building products on a single source of truth for all the business data related to employees. This rich, flexible data source unlocks a powerful set of capabilities.

Permissions
Automatically govern what each person in your company can see, do and access.
Policies
Build custom policies that enforce your business’s unique rules and procedures.
Workflows
Automate virtually anything with hyper-custom triggers and advanced workflow actions.
Analytics
Make better decisions faster with real-time, unified data in an easy-to-use report builder.
Resources
Take a look under
the hood
FAQs
What is identity and access management software?

Identity and access management software centralises the management of user identities and their access to various systems and applications. It ensures that the right people have the right access at the right time.
IAM software can be deployed on-premises, in the cloud or hybrid environments.
How do I choose the right IAM solution?

When choosing an identity access management solution, consider key factors such as:
- Integration: Look for a platform that seamlessly integrates with your existing HR, IT and application ecosystem.
- Automation: Prioritise solutions that automate user lifecycle management, from onboarding to offboarding. Rippling automates provisioning, deprovisioning and access updates based on HR data.
- Security: Ensure the solution offers strong security features such as multi-factor authentication, role-based access control and behavioural detection.
- Scalability: Choose a solution that can grow with your organisation. Rippling’s platform is designed to scale with businesses of all sizes.
- User experience: Look for a self-service platform that makes it easy and intuitive for all team members to use.
Why do organisations need an identity and access management solution?

Organisations need IAM solutions to optimise security by controlling access to sensitive data and applications, streamline user lifecycle management, improve regulatory compliance, minimise the risk of data breaches and centralise management of workforce identities.
What is least privilege access?

Least privilege access is a security principle that grants users only the minimum level of access they need to perform their job functions. Rippling helps enforce least privilege by allowing you to define granular access controls based on roles, departments and other attributes.
What Is Zero Trust?

Zero Trust is an identity security model that assumes no user or device should be trusted by default, regardless of their location or network. This improves your organisation’s security posture by ensuring that every access request is verified and authorised, regardless of where it originates.



















































































































