Policies
Enforce and automate security policies across your org
Easily create, deploy, and enforce custom policies across apps and devices.
Trusted by 6,000+ customers










Supergroups
Apply policies to the right users automatically
Apply policies to users using Supergroups, dynamic membership lists you can customise using attributes like department, start date, or security status. If an employee moves or changes roles, their policies update automatically.
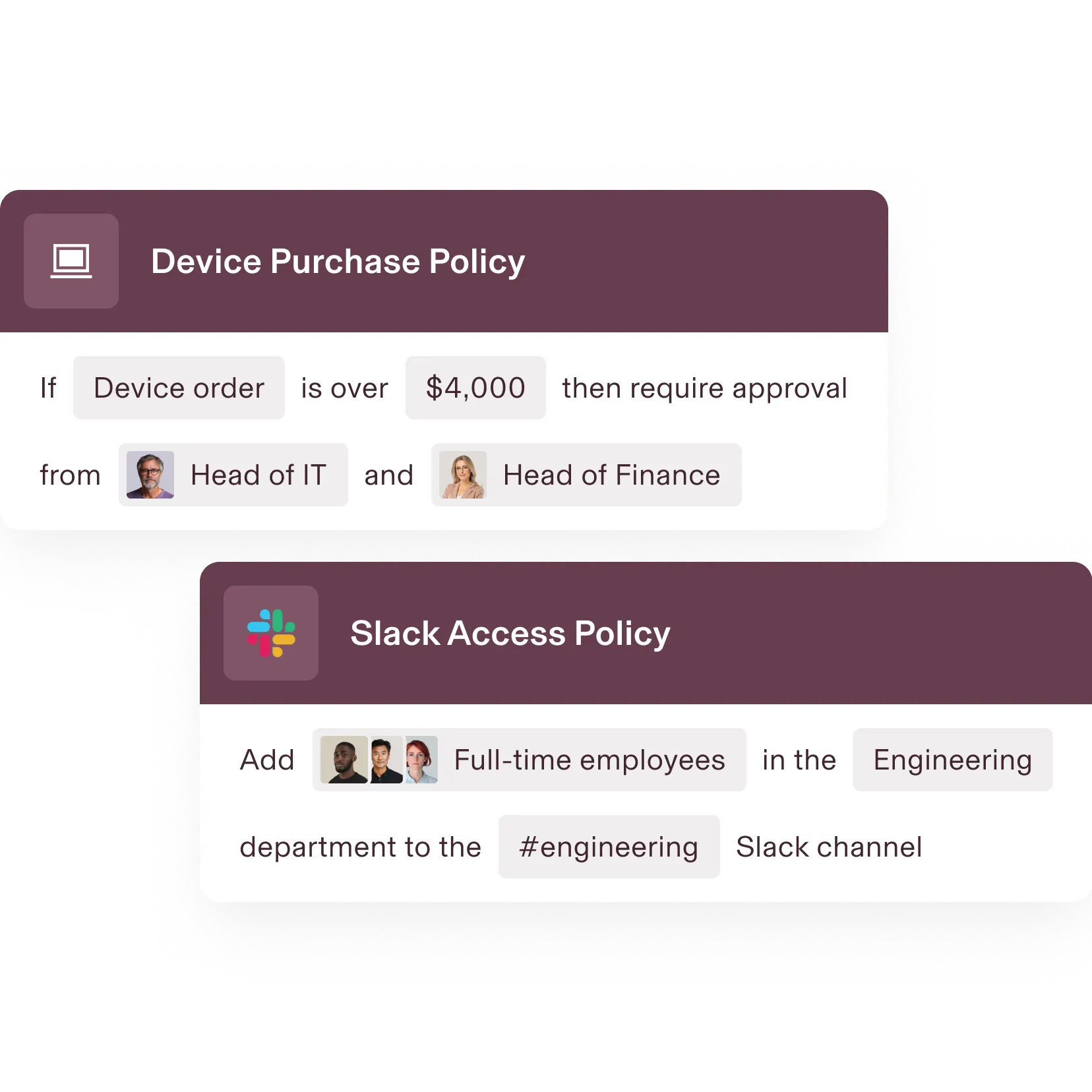
Policy CREATION
Customise policies to meet compliance needs
Rippling makes it easy to meet compliance and security requirements—applying your policies dynamically, so you never have to manually maintain who’s attached to each policy.
Access Policies

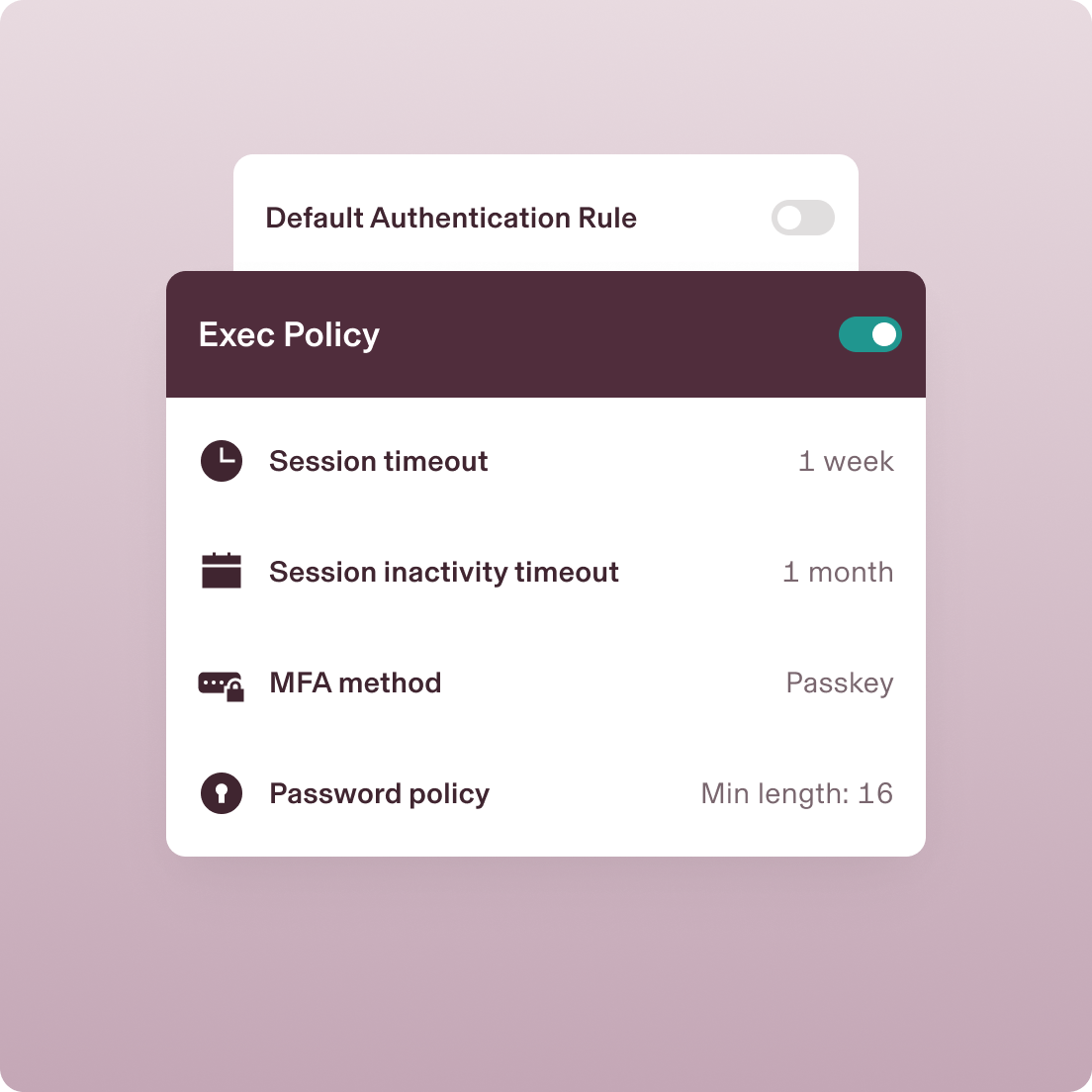
Device Policies

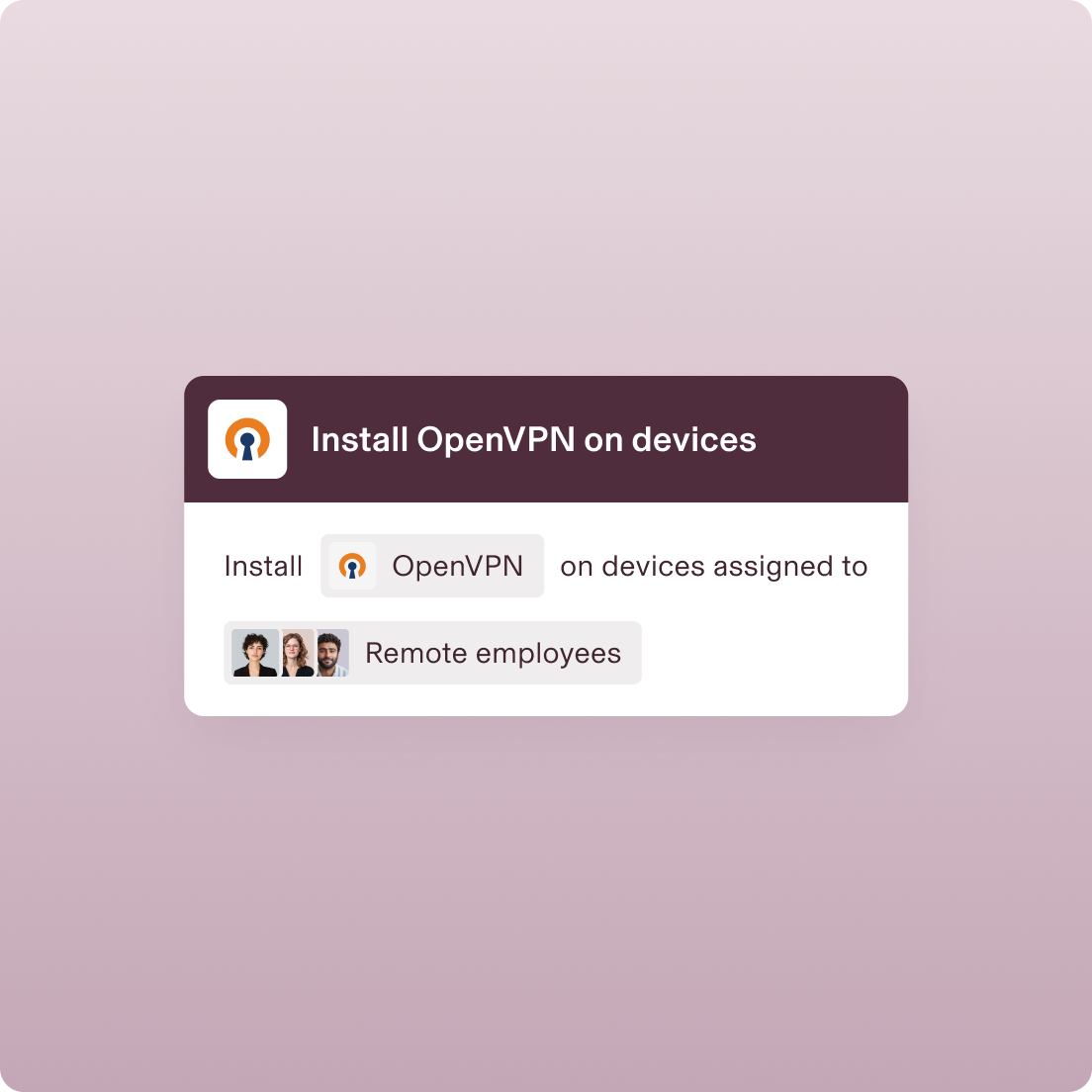
Zero-Trust Policies

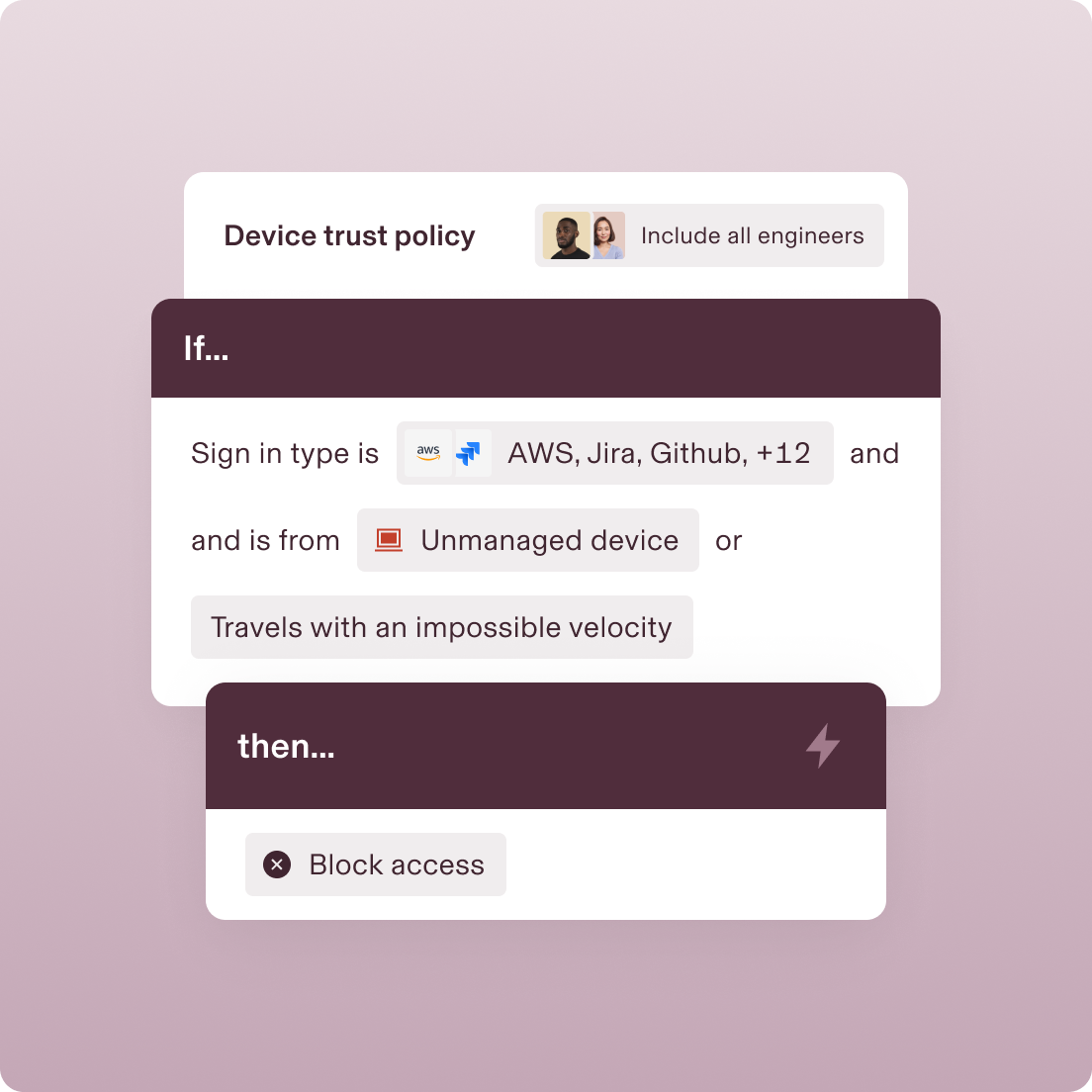
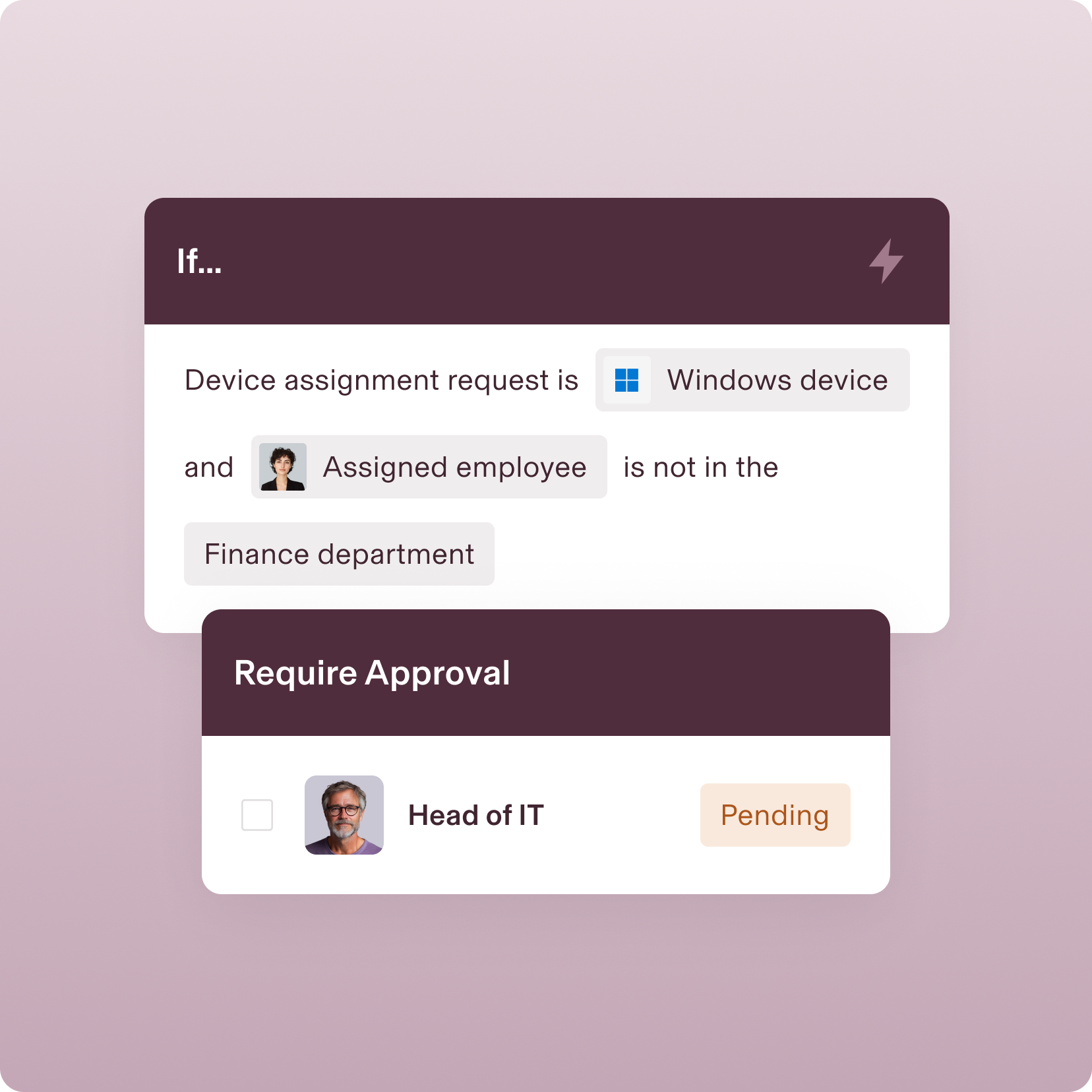
POLICY ENFORCEMENT
Customise policies based on any attribute
Ensure nothing slips through the cracks with automated policy enforcement based on any possible attribute, like device operating system, user role, location, and more.
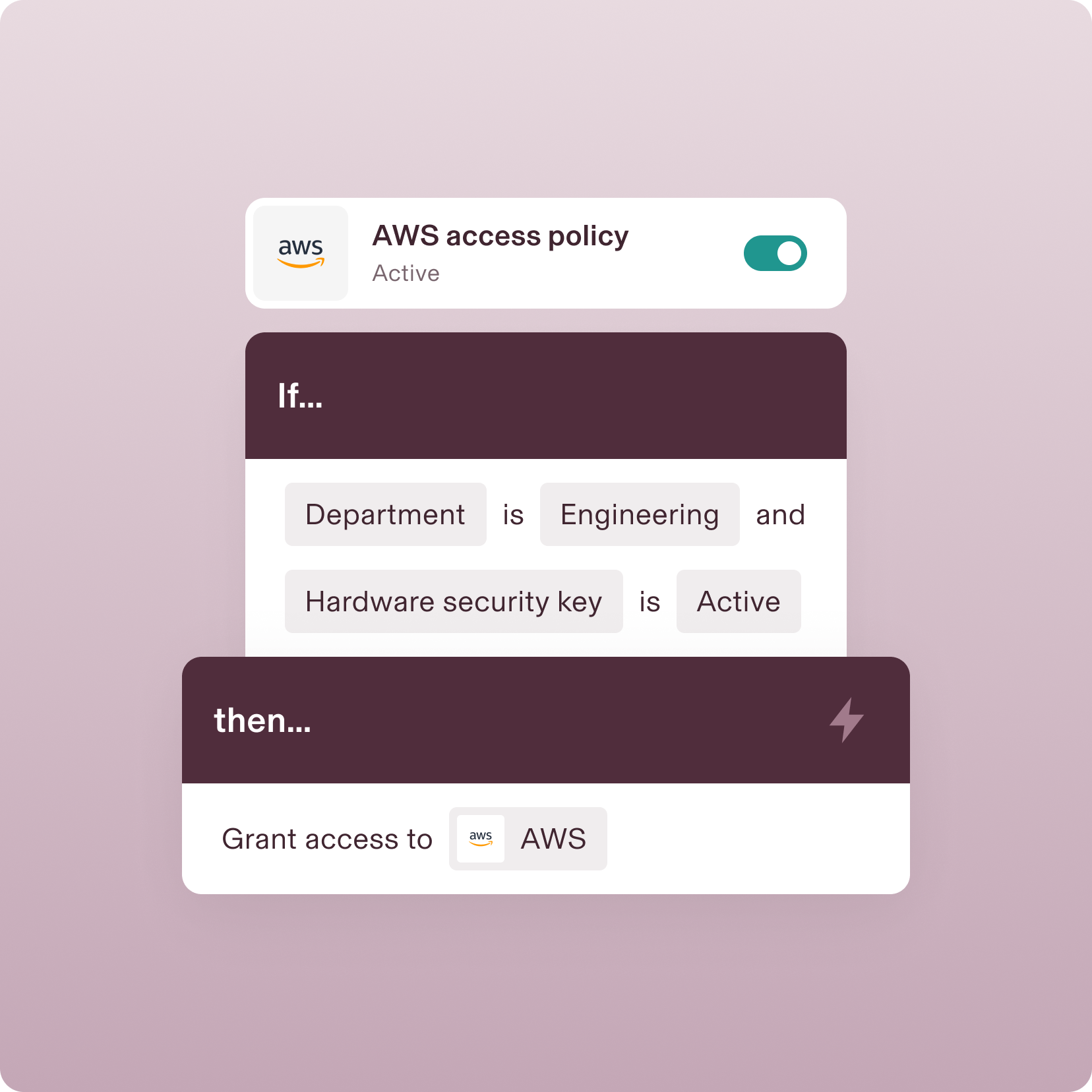
ROLE-BASED POLICY AUTOMATION
Update access when roles change—automatically
With Rippling, the correct policies are automatically applied when a user moves into a new role or Supergroup—no action needed from you.

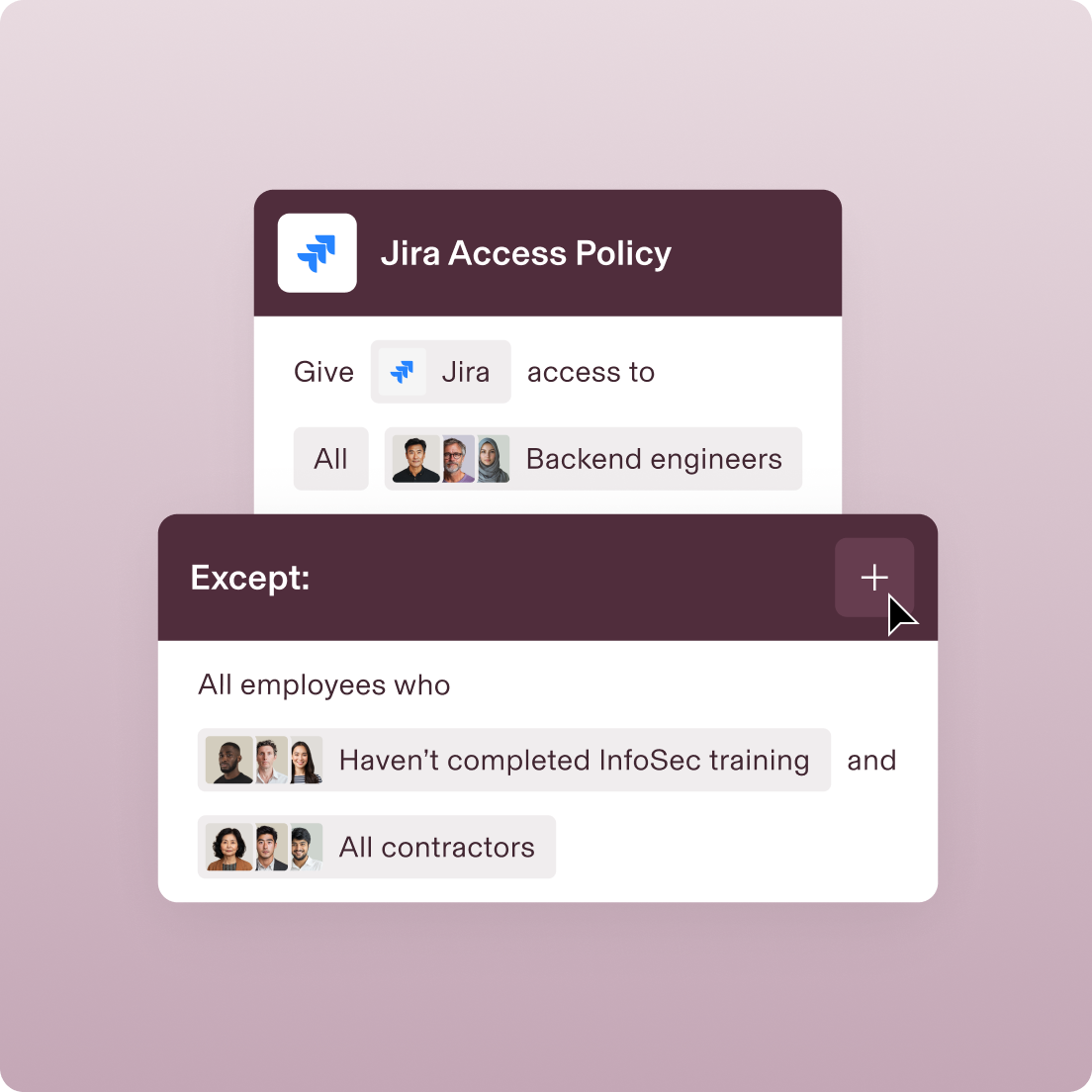
Cross-app policies
Create policies that span your tech stack
A policy triggered in one part of Rippling can enforce actions in another. For example, you can build a role-based access control that prevents engineers from getting Jira access if they haven’t completed their infosec training.
built different
The most efficient way to run IT
Take the effort out of IT with custom workflows, dynamic permissions and policies, and rich reports for users and devices.

Permissions
Automatically govern what each person in your company can see, do, and access.
Policies
Enforce your business’ unique rules with custom policies built on dynamic groups of users.
Workflows
Automate virtually anything with hyper-custom triggers and no-code workflows.
Analytics
Make better decisions faster with real-time, unified data in a report builder.
FAQs
What is rostering software?

Rostering software is a tool that allows managers to create, assign, and adjust work schedules for employees, providing real-time visibility and compliance with labour laws.
How does rostering software improve productivity?

Work rostering software improves productivity by allowing managers to create, assign, and adjust schedules in real-time, helping your business meet operational needs and maximises productivity. It also provides your employees with visibility into their schedules and the ability to request changes, which enhances communication and reduces scheduling conflicts.
How does Rippling simplify rostering for my business?

Rippling simplifies rostering for businesses by integrating rostering with time tracking, payroll, and compliance management into a single platform. This eliminates manual work, and ensures compliance with local labour laws.
What are the benefits of using rostering software?

The benefits of using rostering software include efficient shift management, employee flexibility, real-time schedule tracking, extra compliance safeguards, operational efficiency, and flexible staffing.

See Rippling IT in action
See how you can securely manage identity, access, devices, and inventory all from one platform






























































































































