Rippling IT Management Software
Strengthen security.
Squash busy work.
Rippling IT's management platform is powered by native user and device data, unlocking total visibility and control over Identity, Devices, and Inventory across the user lifecycle.




#1 IT management on Capterra
5000+ IT Customers
#1 Single Sign-On (SSO) on G2
Top Rated on Expert Insights
Category Leader on CTO Club



Native solutions and integrations
Control the entire user life cycle in one system with fully built Identity, Device, and Inventory management tools, and 500+ integrations—including custom SCIM and SAML.
Built to operate your way
Custom workflows, permissions profile, policies, and reports let you manage IT as hands on, or as hands off, as you want.
Give everyone a single source of truth
Unite your IdP and HRIS (Human Resource Information System) on a universal data set to leverage hundreds of user and device attributes—no manual data reconciliation or integration building needed.
Rippling helps IT teams of any size punch above their weight
Centralize your systems
Natively-built Identity, Device, and Inventory management tools cut down your integrations.
Cut admins work in half
Non-Rippling customers have to hire at least 50% more admins to handle work that Rippling automates.
Strengthen your security posture
Native data allows for granular policies you can apply across your entire organization in just a few clicks.
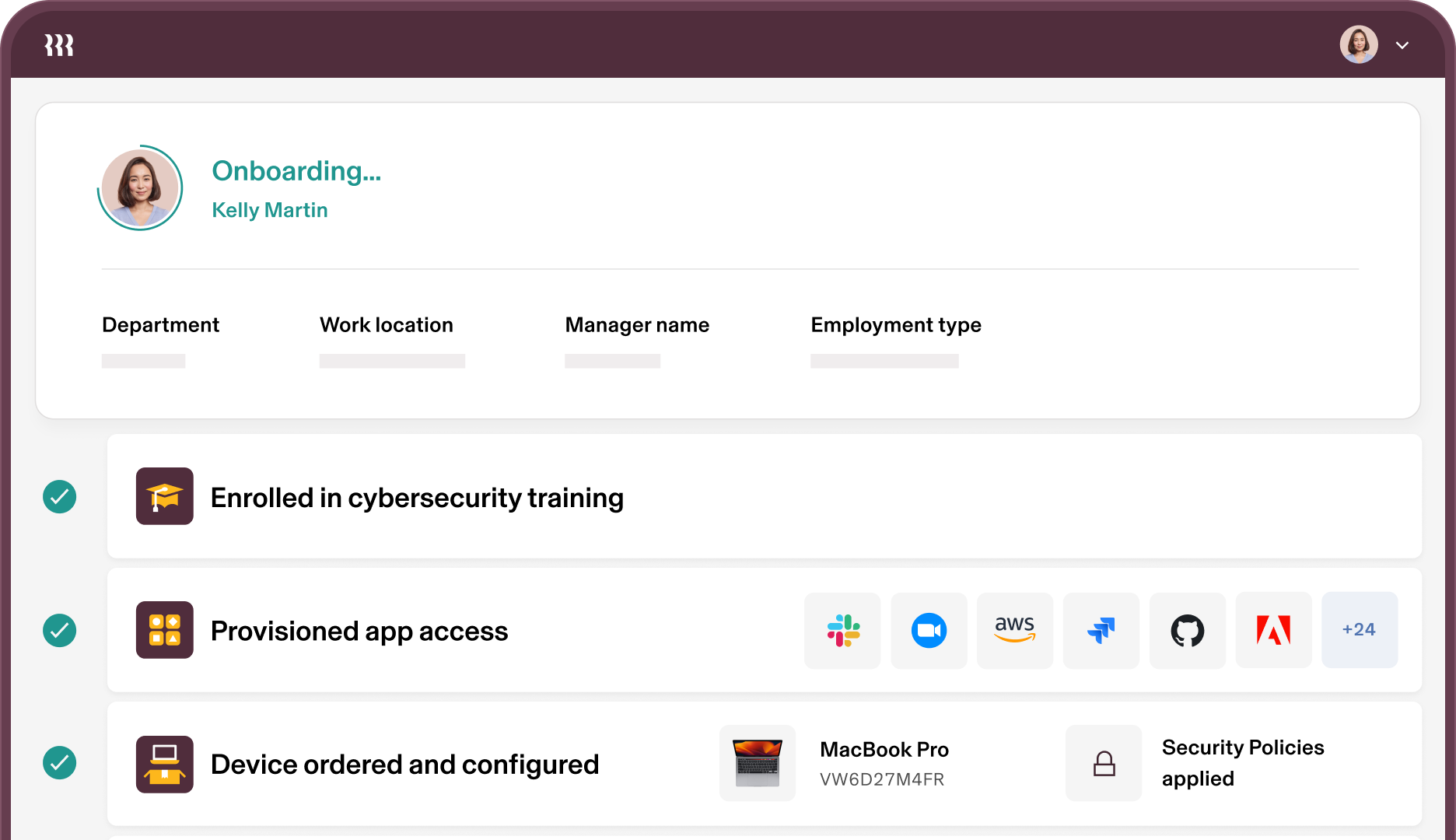
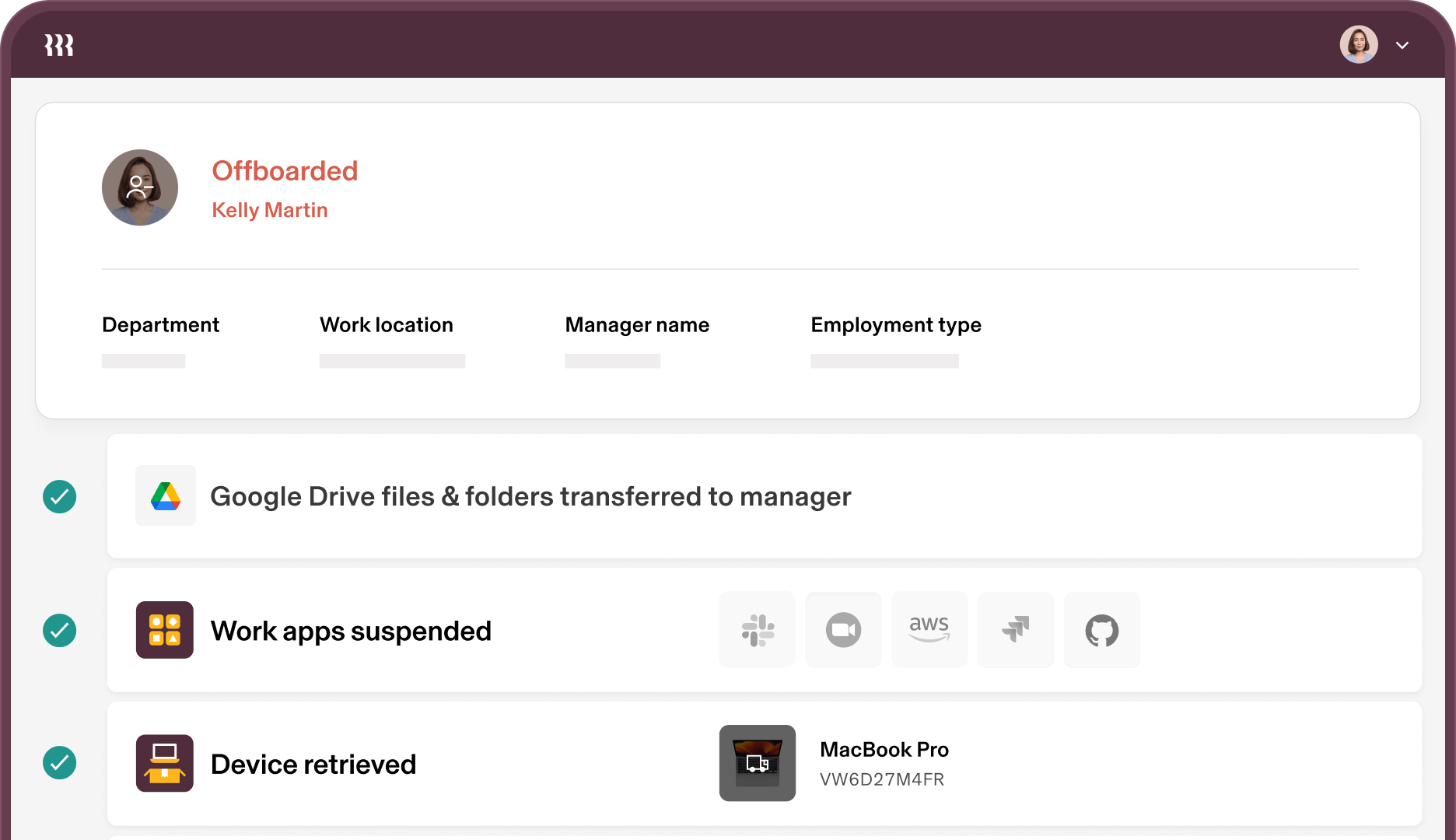
Automate the entire user life cycle
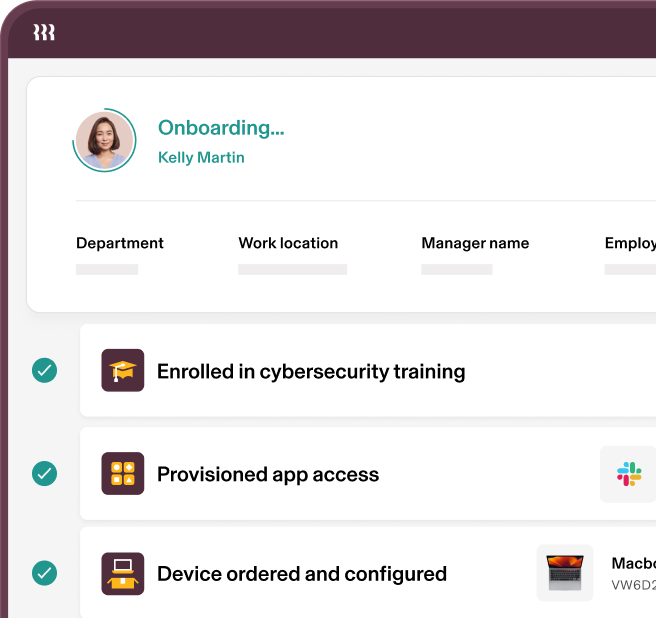
Maintain security from onboarding to offboarding, and every transition in between, with policy automations for provisioning, Single Sign-On, permissions, and devices.
Onboarding

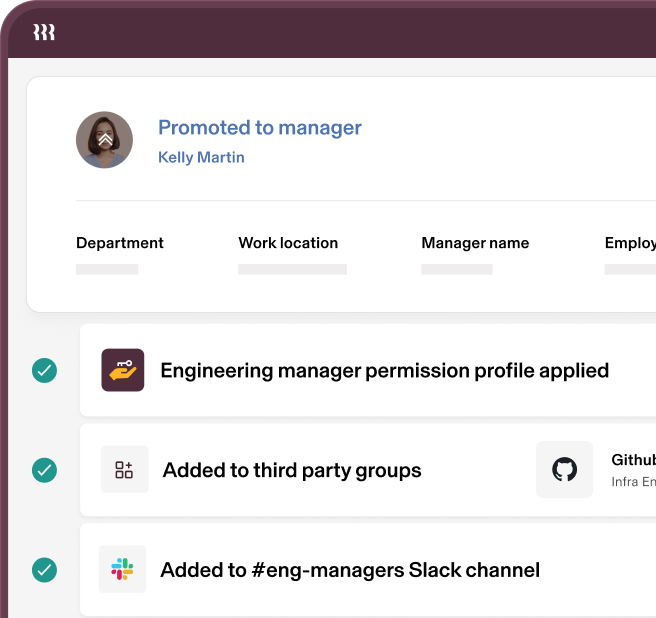
Transitions

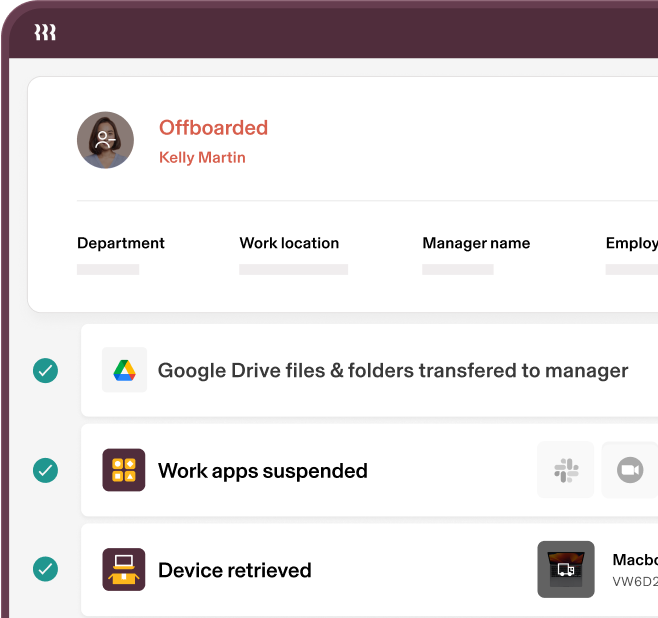
Offboarding

You make the rules. Rippling enforces them.
Deploy custom security policies based on real-time user and device data—like department, operating system, and hundreds of other attributes—that scale automatically across your entire organization.
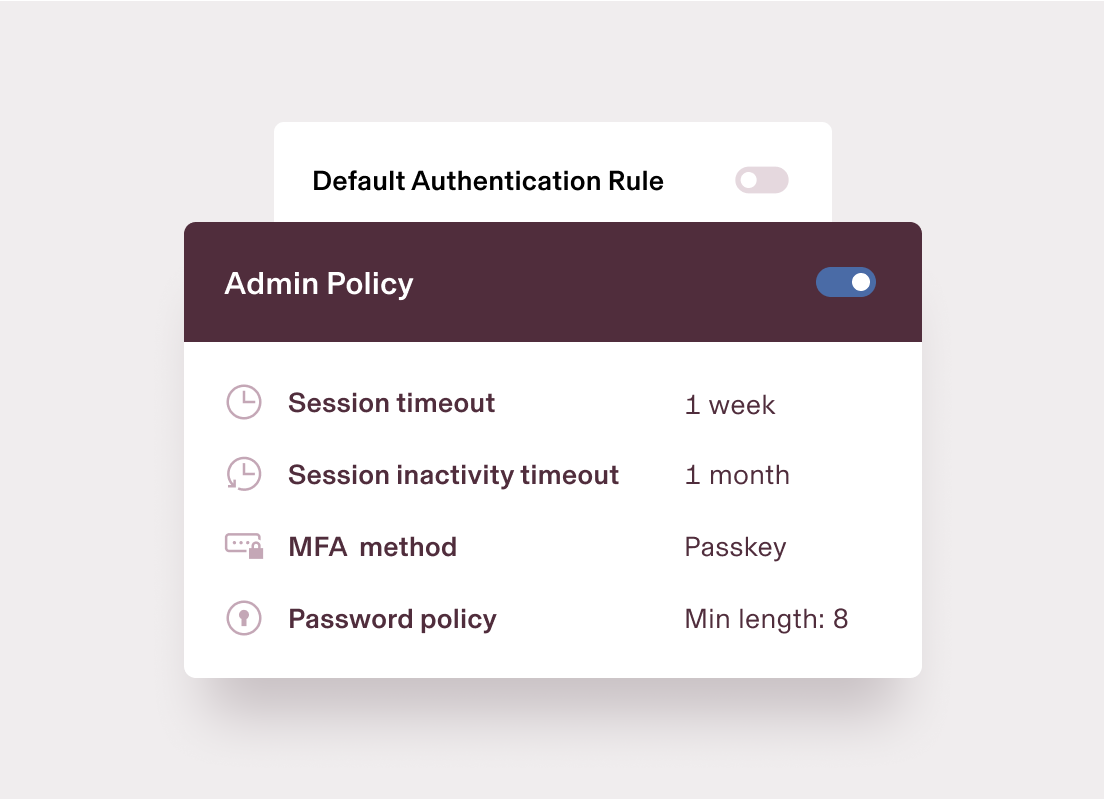
Enforce dynamic authentication
Security polices shouldn’t be a one-size-fits-most solution. Tailor authentication requirements around granular data, like role and department.
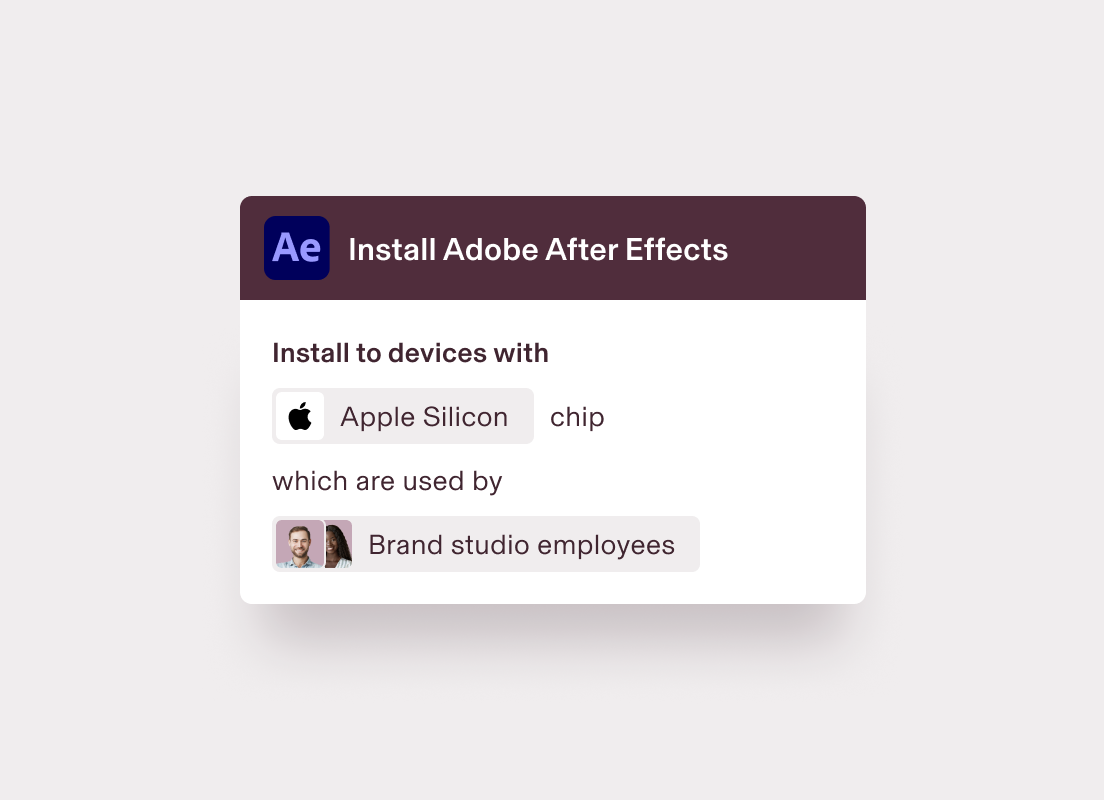
Simplify device configuration
Deploy software, policies, and configurations to devices based on dynamic sets of shared user and device attributes, like OS, department, and encryption status.
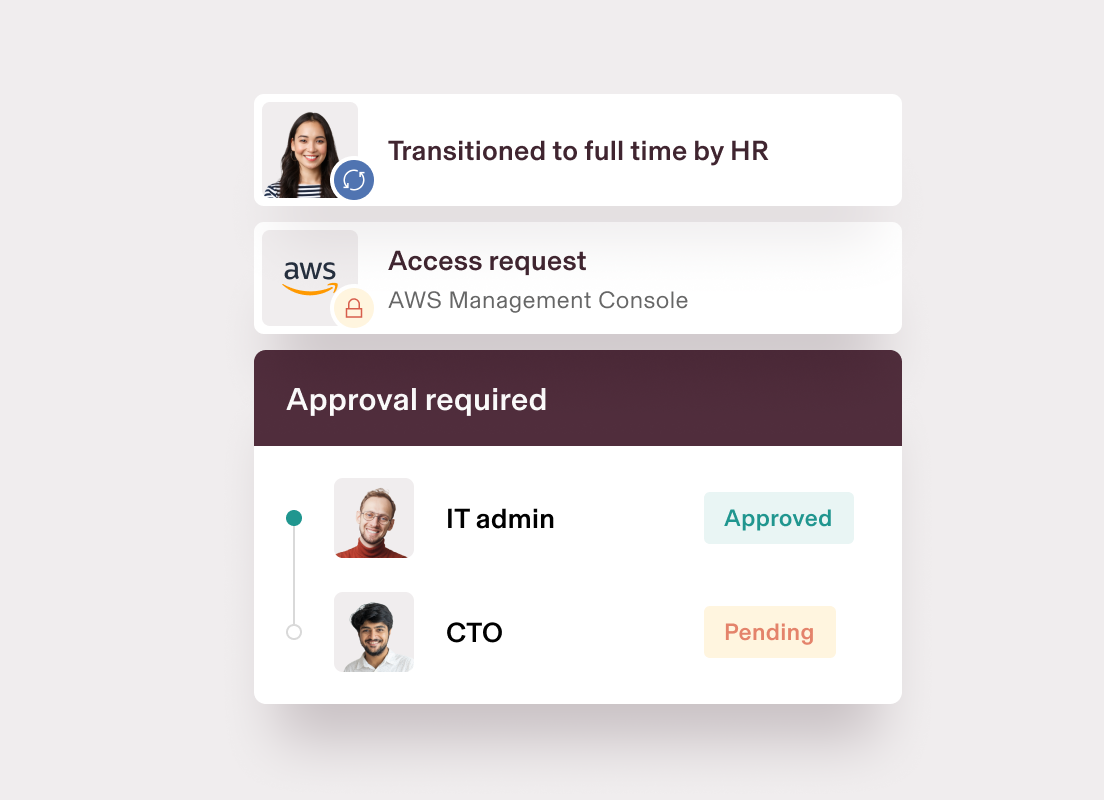
Control system changes
Automatically route requests to the right approvers and craft dynamic policies to ensure seamless collaboration between IT and HR.
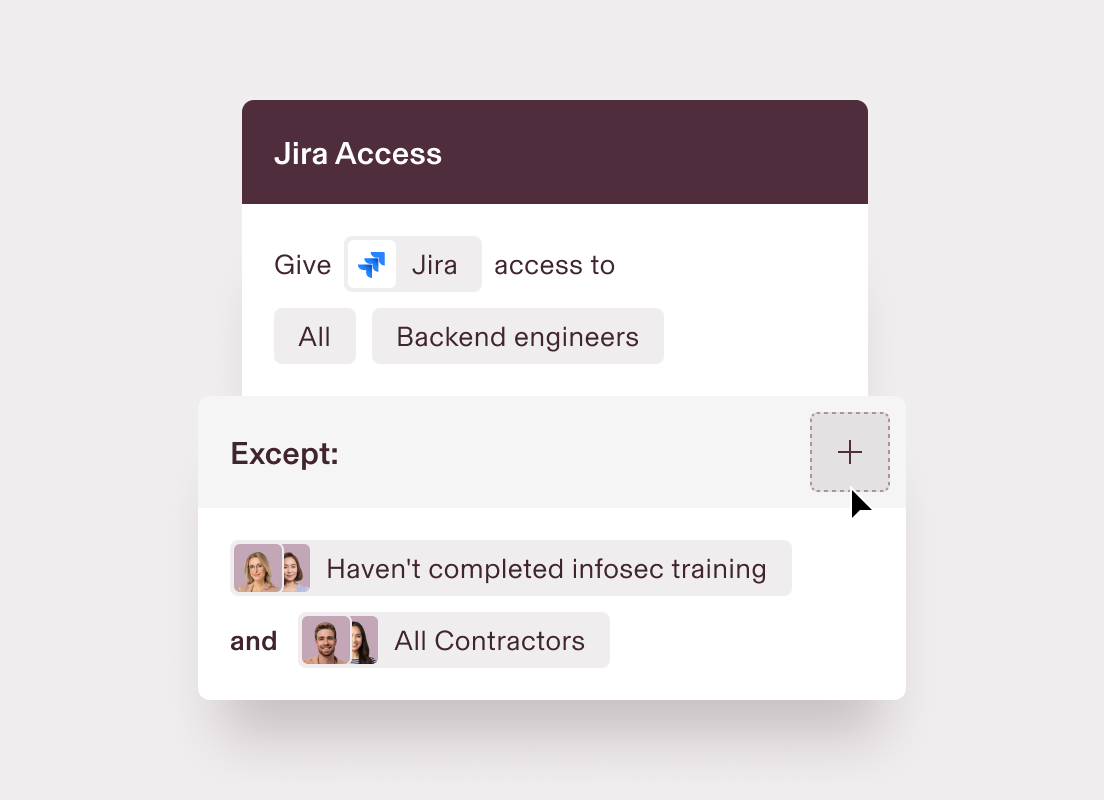
Keep access up to date
Permissions are updated automatically, ensuring everyone has the right level of access without any manual work for your team.
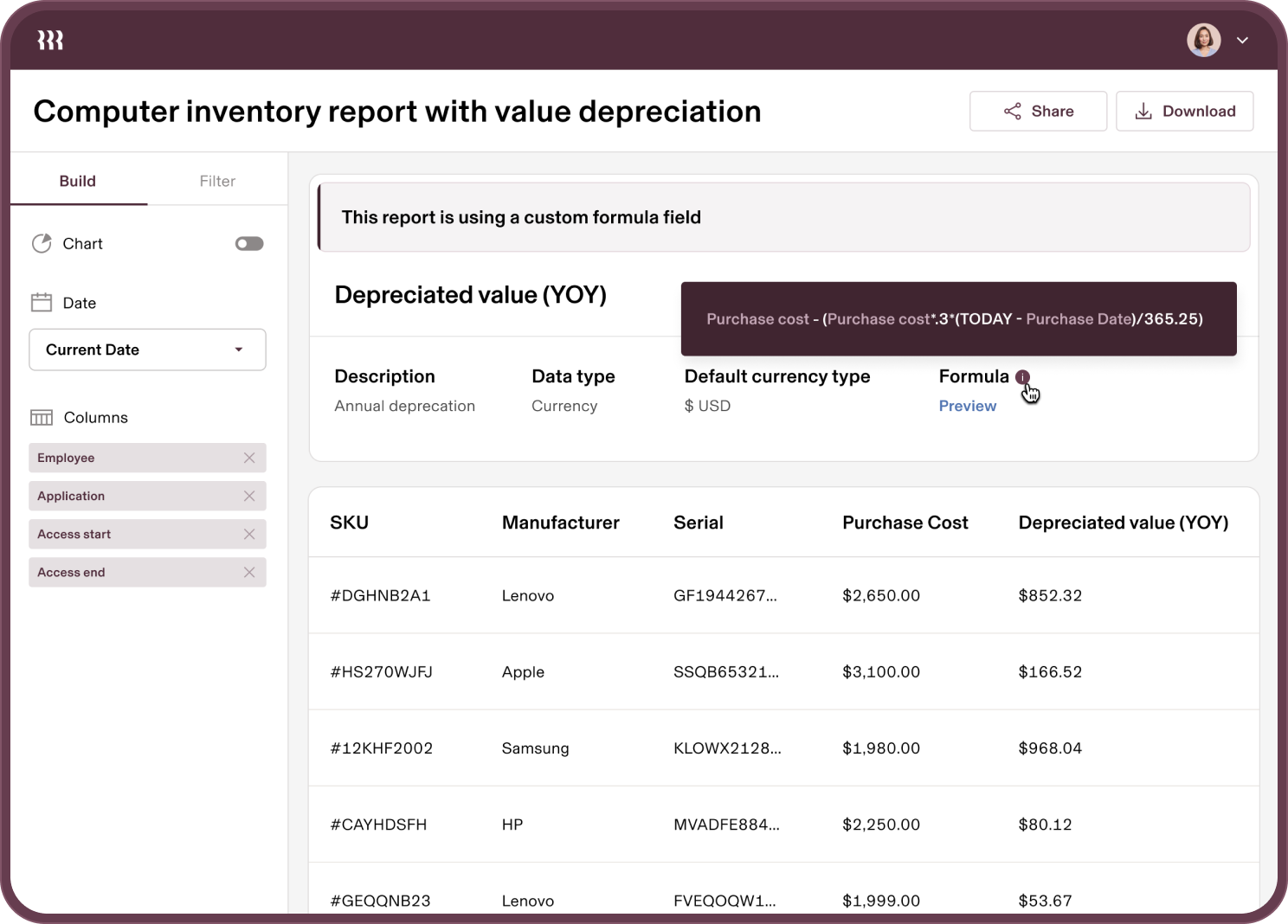
Single pane of glass
End-to-end visibility
Get at-a-glance status updates across identity, access, devices, and inventory. Run reports, track activity, or dive deeper into user and device data.
WORKFLOWS
Free yourself from
manual admins
Create custom workflows triggered by any user or device data to automatically stay in the know across your fleet—for less fire drills, and more happy hours.
Detect suspicious activity

Keep your remote teams secure with behavioural based triggers that require Multi-factor authentication if suspicious IP addresses are detected.
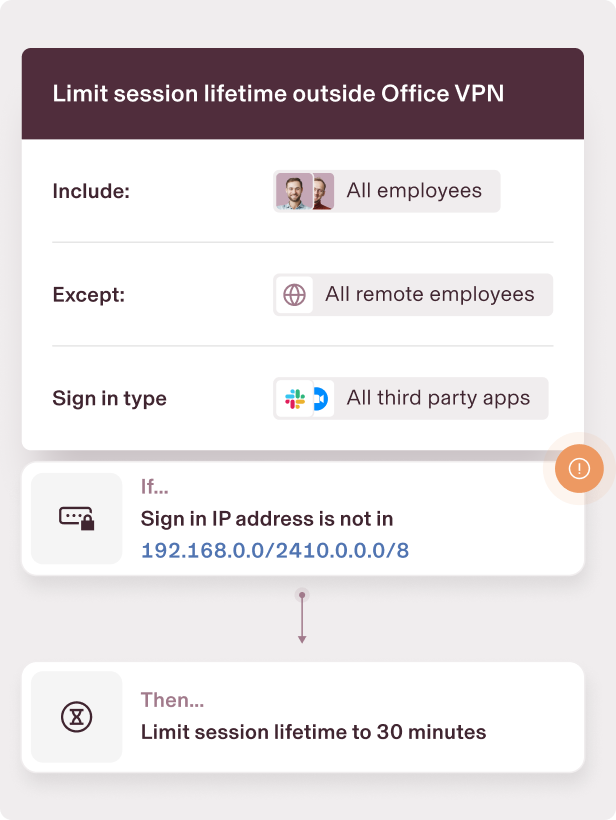
Monitor your fleet

Create granular workflows based on real-time fleet data—like automated notifications for managers and employees if a device doesn’t check-in.
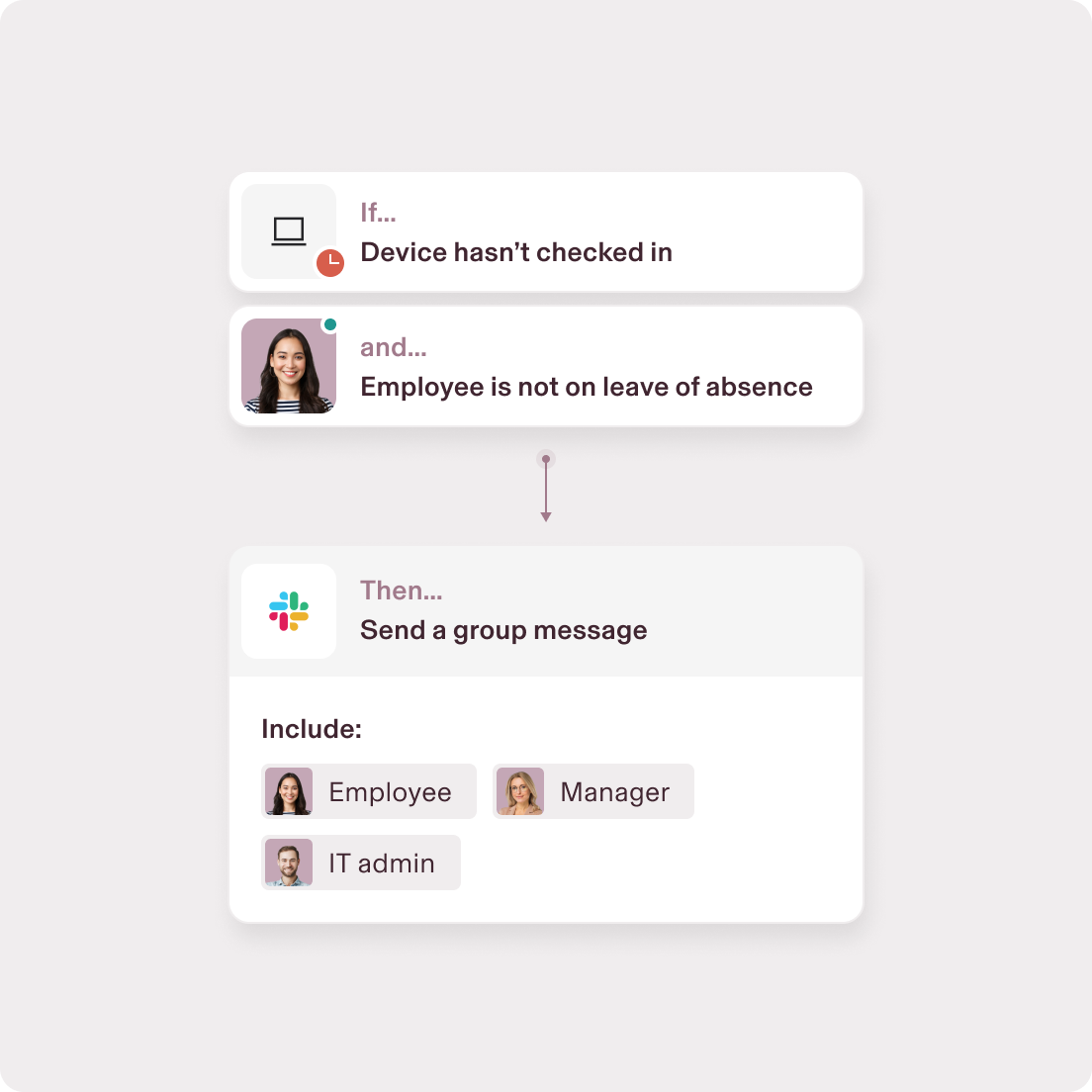
Stay on top of retrievals

Set rules to automatically trigger device retrieval and storage in one of Ripplings’ device warehouses.
END TO END SECURITY
All the security tools you need—and then some
User provisioning & Single Sign-On
Role-based access controls
Activity audit logs
Multi-factor authentication & password enforcement
Cross-OS MDM
Compliance Reporting
Endpoint management and protection
OS & software updates



SOC 2 Type II, ISO 27001, CSA STAR Level 2
Rippling combines enterprise-grade security features with regular audits to ensure that your data is always protected.
Learn more about securityEND TO END IT SOFTWARE
Native tools for the entire user and device life cycle
All
Device management
Identity & Access
Inventory management
Built different
Analyze, automate, and orchestrate anything
Most "all-in-one" software consists of acquired systems. These modules are disconnected, so your business data is, too. Rippling takes a platform approach, building products on a single source of truth for all the business data related to employees. This rich, flexible data source unlocks a powerful set of capabilities.

Permissions
Automatically govern what each person in your company can see, do, and access.
Policies
Build custom policies that enforce your business’s unique rules and procedures.
Workflows
Automate virtually anything with hyper-custom triggers and advanced workflow actions.
Analytics
Make better decisions faster with real-time, unified data in an easy-to-use report builder.
Resources
Take a look under
the hood

See Rippling IT in action
FAQs
What is information technology (IT) management software?

IT management software is a cloud-based solution designed to provide IT departments with centralized control and visibility over their technology and device ecosystem.
With IT management software, there are no more disparate monitoring tools, repetitive tasks, or manually intensive processes. Instead, IT teams can optimize their workflows, enforce consistent policies, and gain end-to-end visibility into their IT environment. This allows for streamlined IT operations, enhanced cybersecurity, and automation across the entire user lifecycle, from onboarding to offboarding.
How can IT management software improve business efficiency?

Implementing an effective IT service management (ITSM) solution can significantly improve business efficiency by automating business processes and centralizing IT asset management. IT management software automates crucial processes like user provisioning, software deployments, and offboarding procedures.
When IT departments are freed of the administrative burdens of device, inventory, and asset management, they can facilitate faster troubleshooting, minimize downtime, and ensure consistent policy enforcement—which all contributes to a more secure and stable IT infrastructure.
How do I choose the right IT management software for my business?

Choosing the right IT management platform requires careful consideration of your organization's unique business needs and existing IT environment. Look for:
- Unified data architecture that can provide comprehensive coverage across identity & access, device management, and inventory management
- Automation that can streamline key workflows and enforce granular security policies
- Scalability to ensure the software can adapt to your growth
- Integrations with your existing ecosystem of applications
- Security and compliance certifications (like SOC 2 and ISO 27001)
- A self-service user experience that makes it easy for any team member to use, regardless of technical expertise