Obtenez une vision en temps réel de votre posture en matière de sécurité grâce à des données sur les appareils et les utilisateurs à portée de main.
Une seule solution pour sécuriser tout votre parc
Renforcez la sécurité et simplifiez la gestion des appareils grâce au seul logiciel MDM qui offre un accès en temps réel aux données natives des utilisateurs et des appareils.


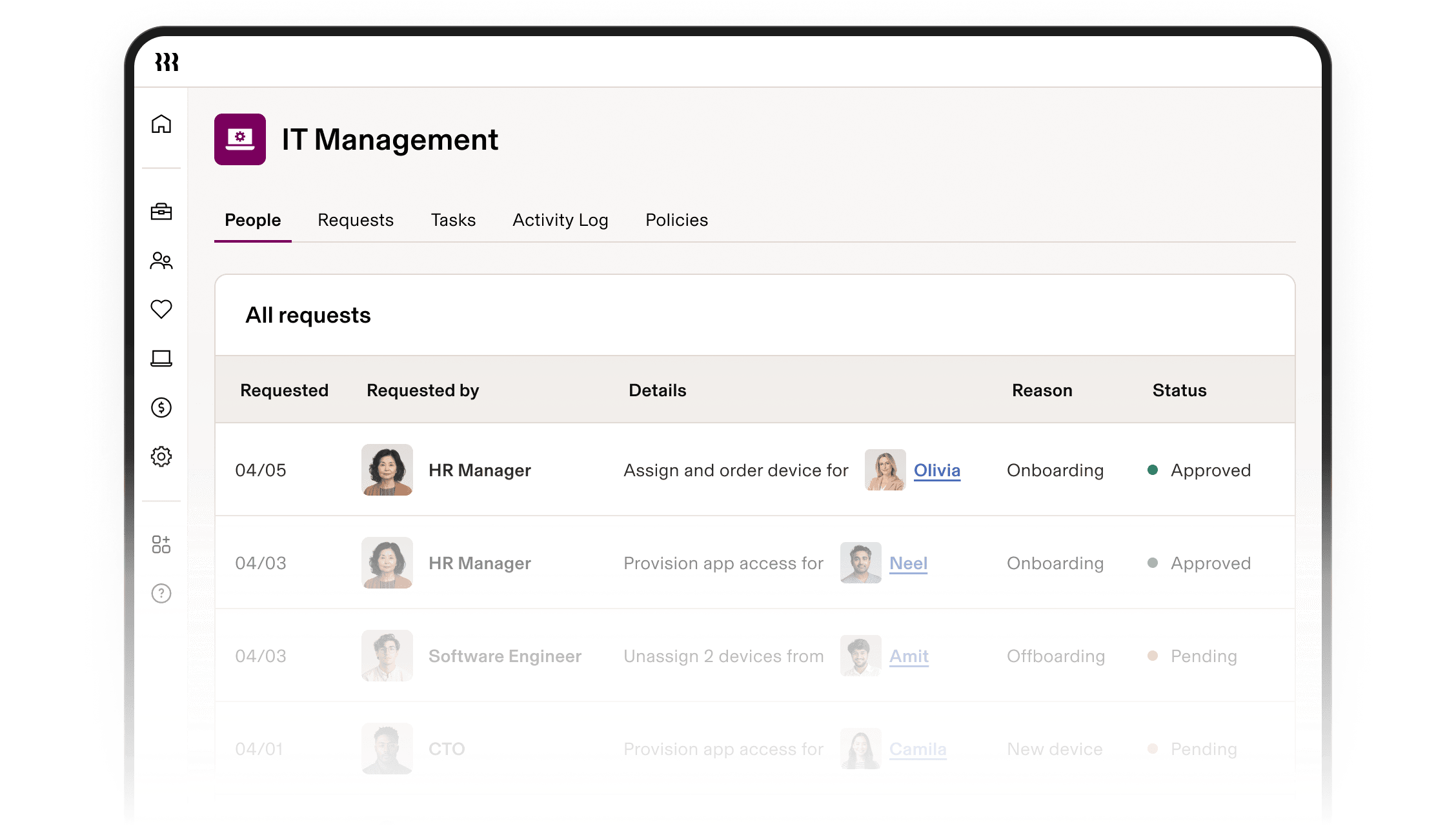
Référence unique pour tous vos appareils
Grâce aux données natives sur les utilisateurs et les appareils, vous pouvez élaborer des politiques détaillées pour un contrôle total de la sécurité des appareils. Aucune intégration SCIM ou extraction manuelle de données n’est nécessaire.
Simplifiez la gestion des appareils grâce à des automatisations pour l’ensemble du cycle de vie des appareils Apple et Windows.
Élaborez et appliquez des politiques de sécurité personnalisées basées sur des centaines d’attributs d’utilisateurs et d’appareils.
Sécurité sans frictions
Rippling vous offre des contrôles de sécurité précis sur tout votre parc et sur le cycle de vie des utilisateurs, depuis les politiques personnalisées et la surveillance des appareils jusqu’aux rapports détaillés et à la gestion des menaces.
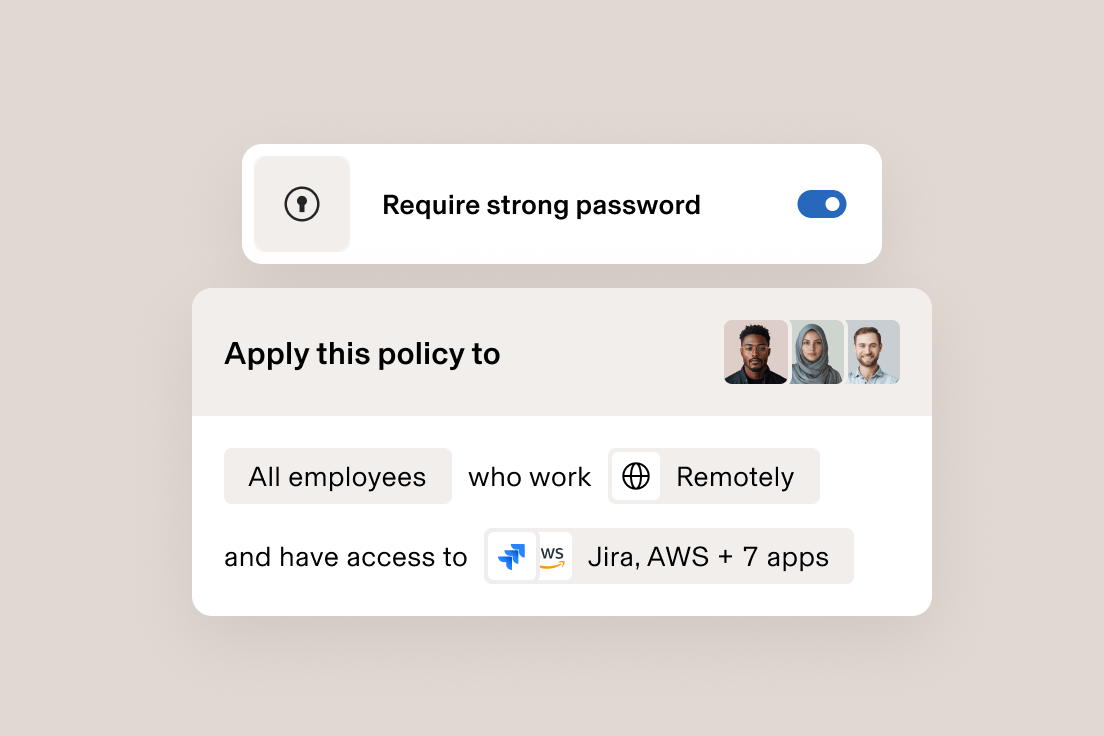
Les politiques de sécurité personnalisées basées sur les attributs des utilisateurs et des appareils sont automatiquement mises à jour pour renforcer la posture en matière de sécurité dans l’ensemble de votre organisation.
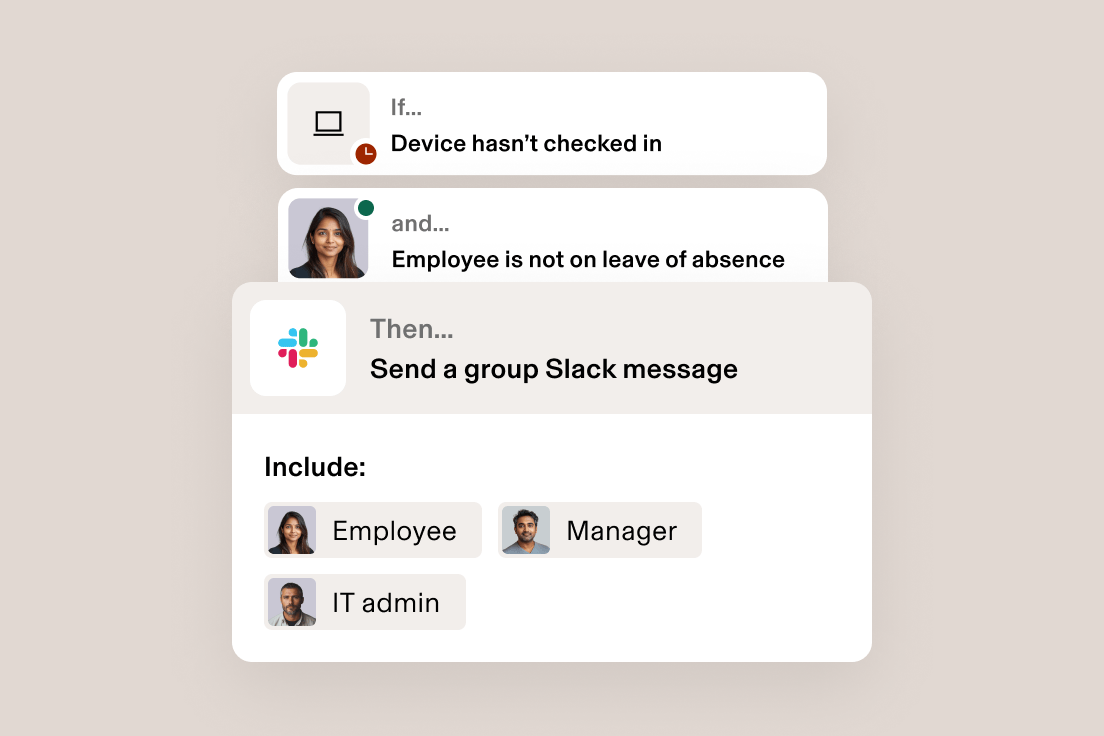
Restez à la pointe de la sécurité. Des workflows personnalisés vous informent automatiquement de toute menace de sécurité, sans qu’il faille vérifier manuellement les appareils ni extraire des données.
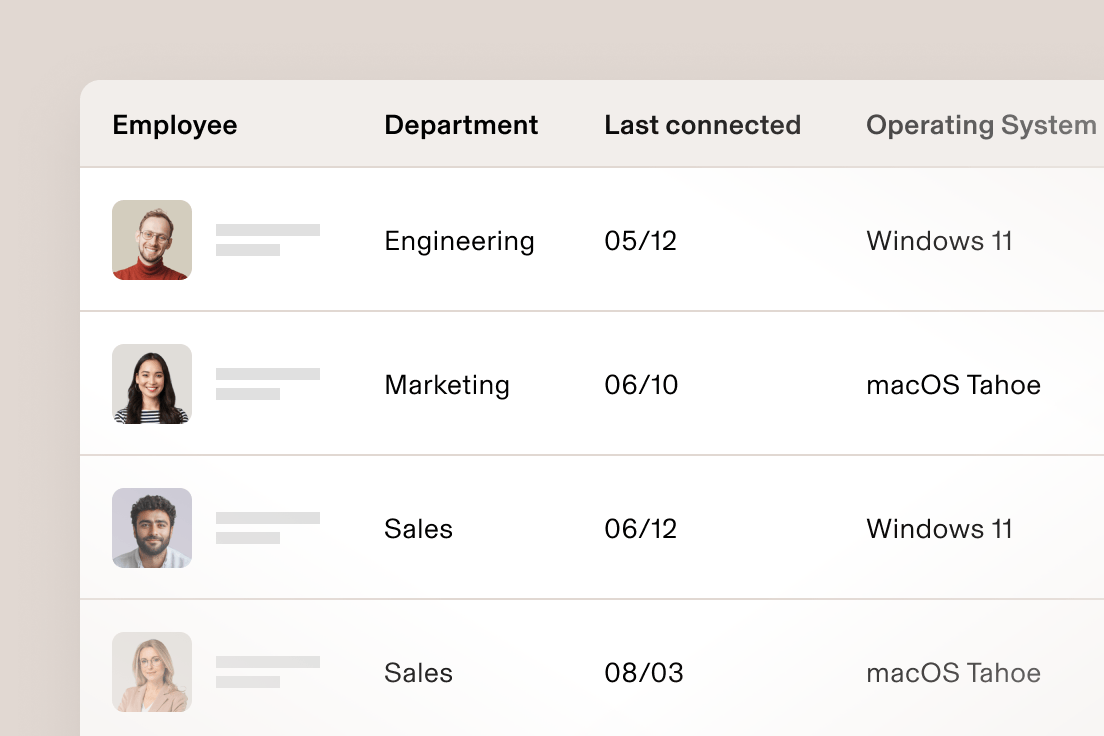
Les rapports personnalisés par pointer-cliquer basés sur des données riches sur les utilisateurs et les appareils facilitent la compréhension de l’état de votre sécurité et l’extraction des données d’audit.

SentinelOne est parfaitement intégré à Rippling pour garantir la sécurisation automatique de tous les appareils avec la meilleure protection des points d’accès.
Des appareils adaptés dès le premier jour
Des politiques d’approbation personnalisées et des flux de travail basés sur des données en temps réel garantissent le contrôle et la synchronisation avec les RH, ce qui vous permet d’intégrer les nouveaux employés avec ou sans intervention, selon vos besoins.
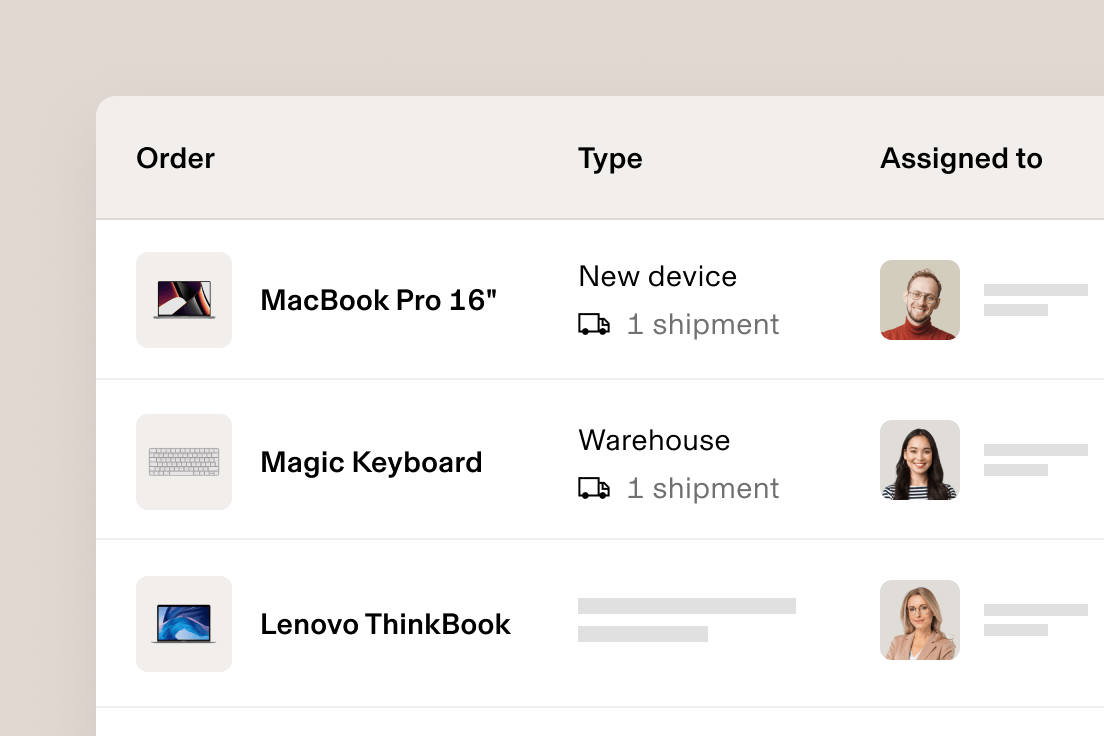
Expédiez en un seul clic. Avec Rippling, vous pouvez commander, réattribuer et livrer des appareils directement aux nouvelles recrues, le tout à partir d’un seul endroit.
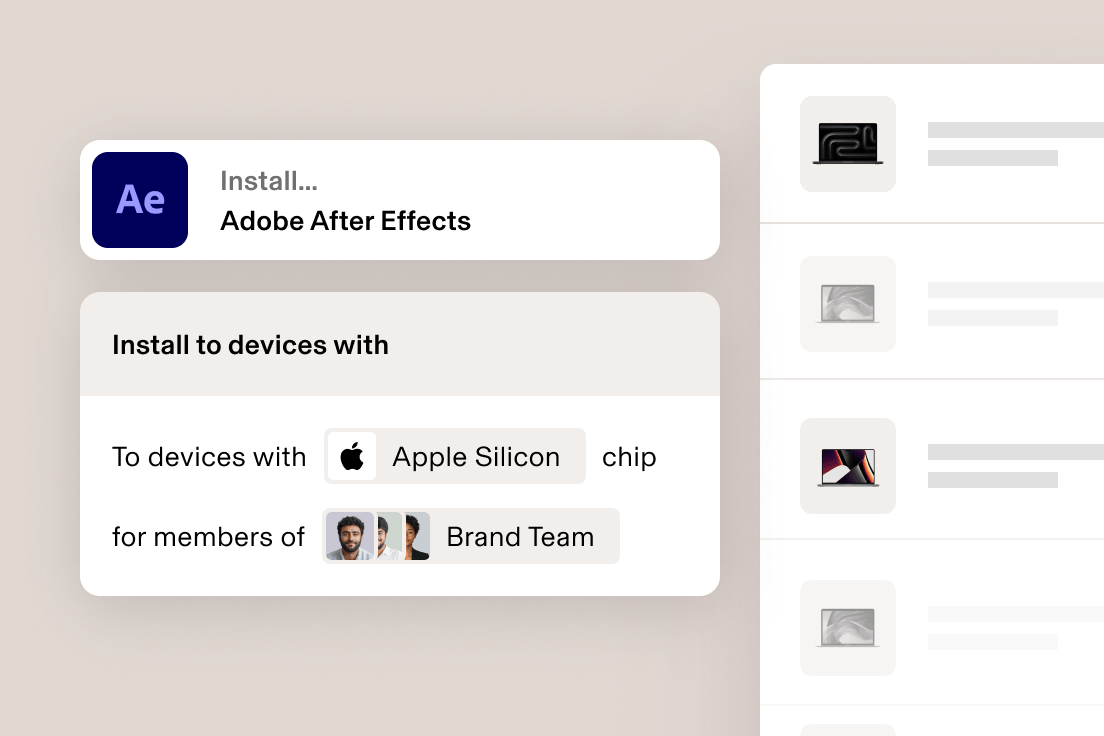
L’enregistrement des appareils est un jeu d’enfants. Configurez automatiquement les ordinateurs portables, les iPhone et les iPad avec les logiciels, les accès et les paramètres de sécurité appropriés en fonction d’attributs comme le site, le service et le rôle.
Des départs en toute sécurité
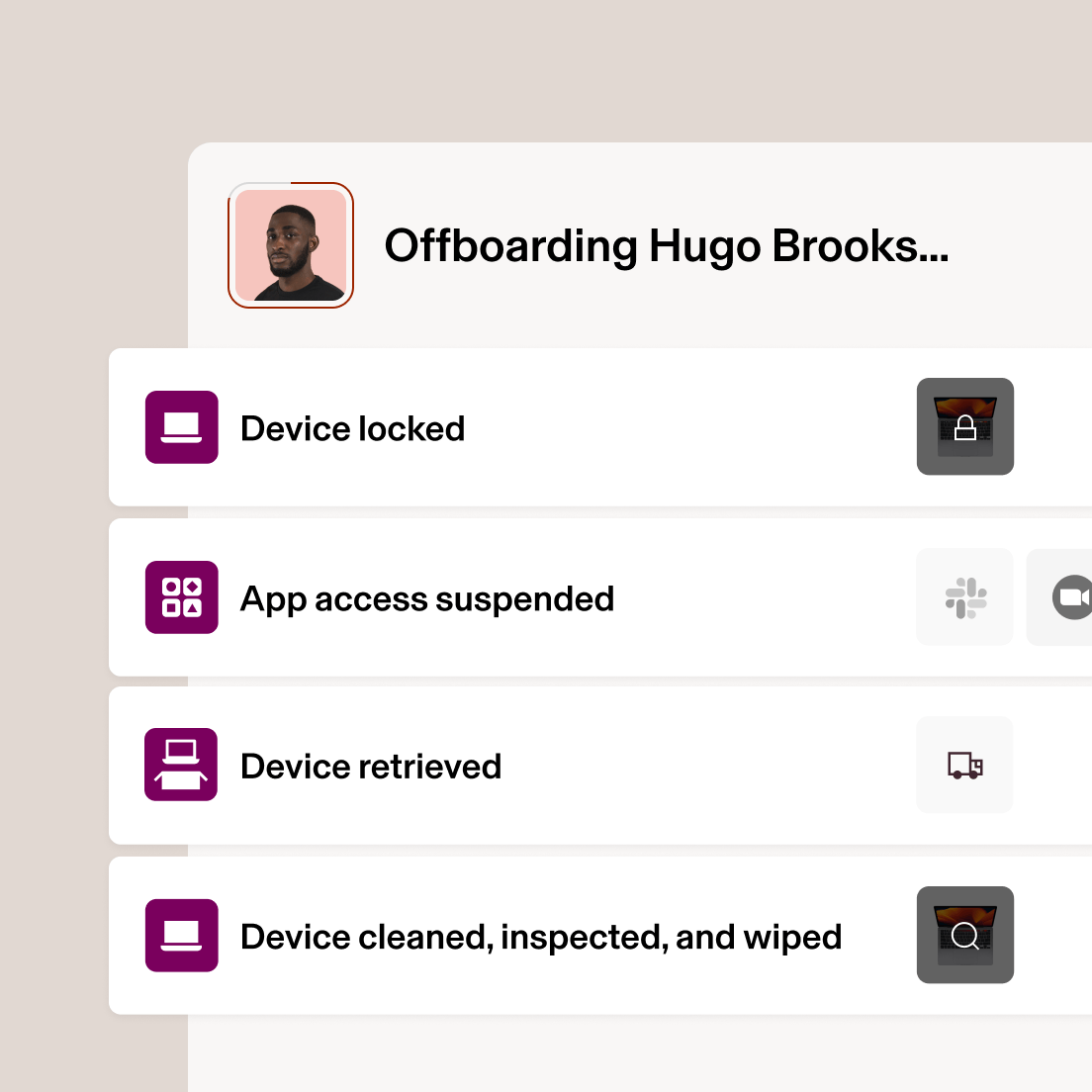
Récupérer les appareils des collaborateurs peut rapidement devenir un risque pour la sécurité, surtout s’ils travaillent à distance. Rippling vous facilite la tâche en automatisant l’offboarding des appareils de A à Z.
- Effacez et verrouillez les appareils instantanément
Comme vous êtes automatiquement synchronisé avec le processus de fin de contrat des RH, vous pouvez planifier l’heure exacte à laquelle verrouiller et effacer un appareil.
- Automatisez la récupération des appareils
Finis les déplacements au bureau de poste, la logistique d’expédition fastidieuse et les appareils perdus. Rippling gère automatiquement l’enlèvement.
- Stockez en toute sécurité les appareils inutilisés
Entreposez vos appareils dans les installations sécurisées de Rippling à travers le monde au lieu de les stocker dans des armoires informatiques encombrées.
Nous nous occupons de la logistique
Notre solution MDM est bien plus qu’un simple logiciel. Rippling s’occupe également des tâches fastidieuses de la gestion du parc.
La manière la plus efficace de gérer l’IT
Simplifiez le travail de votre équipe IT grâce à des workflows personnalisés, des autorisations et politiques dynamiques, et des rapports détaillés sur les utilisateurs et les appareils.
Les entreprises qui utilisent Rippling ont de meilleurs résultats

Tous les outils de sécurité dont vous avez besoin, et plus encore
Gestion des identités et des accès
Rippling propose plus de 600 intégrations à d’autres produits SaaS pour le provisionnement et le déprovisionnement des utilisateurs, l’authentification unique, la synchronisation des attributs et plus encore.
Créez des intégrations personnalisées pour fournir l’authentification unique avec le standard SAML et le provisionnement avec JIT ou SCIM, ou créez et configurez des liens d’URL auxquels les collaborateurs peuvent accéder à partir de la barre d’authentification unique dans Rippling.
Étendez le répertoire des utilisateurs de Rippling (graphe d’objets) à toutes vos applications tierces en aval et maintenez ainsi les données de vos collaborateurs à jour sur tous les systèmes, en temps réel.
Créez des politiques d’authentification sur mesure pour des groupes de collaborateurs ou même des collaborateurs individuels en fonction de leur rôle. Par exemple, vous pouvez exiger des clés YubiKeys pour les administrateurs et des mots de passe temporaires (TOTP) pour les autres collaborateurs. L’authentification est entièrement personnalisable.
Rippling est un revendeur Google, ce qui vous permet de gérer et d’acheter des licences directement dans Rippling pour ces applications. Ne vous retrouvez plus jamais à court de licences lorsque vous créez un nouvel utilisateur.
Bénéficiez d’une fonctionnalité avancée qui automatise le processus pénible d’offboarding d’un collaborateur, du déprovisionnement de son compte Google au transfert de propriété. Réaffectez les fichiers Google Drive, transférez la propriété des événements du calendrier, donnez accès au compte Gmail professionnel des personnes qui partent, supprimez les mots de passe et les informations de récupération propres aux applications, et plus encore.
RPass est le gestionnaire de mots de passe natif de Rippling. RPass permet de stocker facilement et de partager en toute sécurité des mots de passe au sein de votre équipe grâce aux supergroupes, la fonctionnalité de Rippling permettant de créer des groupes de collaborateurs en fonction de n’importe quel attribut. Vous préférez utiliser un autre gestionnaire de mots de passe ? Aucun souci : Rippling s’intègre aussi à l’outil qui vous convient le mieux.
Dans Rippling, tout repose sur le rôle du collaborateur, de l’accès aux applications aux droits d’administration. Donnez à chacun tout ce dont il a besoin, et rien d’autre.
Gérez et organisez l’accès aux clés pour les collaborateurs individuels et les groupes en fonction de n’importe quel attribut de collaborateur. Supprimez automatiquement l’accès dans les moments clés du cycle de vie des collaborateurs, comme un changement de rôle ou une fin de contrat.
Connexion et authentification en un clic à toutes les applications tierces connectées une fois la session ouverte dans Rippling.
Accordez ou suspendez automatiquement l’accès des utilisateurs aux applications et aux licences en fonction de règles prédéfinies que vous créez vous-même. Vous pouvez effectuer le provisionnement instantanément ou le programmer pour qu’il ait lieu ultérieurement.
Transférez en toute transparence les données des utilisateurs de Rippling vers vos applications tierces et vos infrastructures réseau existantes, comme le pare-feu, le serveur de stockage en réseau et plus encore.
Assurez-vous que les collaborateurs ont accès aux ressources et aux groupes appropriés dans d’autres applications et systèmes. Des groupes Google aux canaux Slack en passant par les licences Microsoft, Rippling automatise l’affectation des membres de votre équipe à tous les groupes pertinents au sein de vos systèmes et outils. Grâce aux supergroupes, n’importe quel attribut de collaborateur peut être utilisé pour accorder (et retirer) un accès. Lorsqu’un collaborateur change de rôle ou quitte l’entreprise, son appartenance aux groupes est instantanément mise à jour pour garantir votre conformité.
Gestion des appareils
Attribuez rapidement des appareils à n’importe quel collaborateur et annulez l’attribution tout aussi facilement. Sélectionnez des appareils pour un nouveau collaborateur pendant l’onboarding ou modifiez manuellement les attributions à tout moment, sans quitter Rippling.
Appliquez facilement des paramètres personnalisés tels que des profils Wi-Fi, des configurations de pare-feu, des associations d’imprimantes, des écrans de connexion personnalisés, des arrière-plans, etc. Dans la mesure où ils reposent sur la plateforme Rippling, tous ces paramètres personnalisés peuvent être appliqués de manière dynamique à des personnes ou des groupes en fonction de n’importe quel attribut de collaborateur (le service, l’échelon ou le site, par exemple)
Commandez en toute simplicité tout ce qu’il faut à une nouvelle recrue, directement dans le processus d’onboarding. Rippling est revendeur agréé Mac et PC, ce qui signifie que vous pouvez commander et expédier des appareils en quelques clics. Dites adieu aux expéditions de dernière minute au magasin d’informatique local et aux services FedEx.
Utilisez des scripts Bash (macOS) et Powershell (Windows) pour personnaliser davantage vos appareils. Exécutez les scripts de manière ponctuelle ou récurrente, puis affichez ou exportez le résultat.
Utilisez le serveur RADIUS hébergé de Rippling pour permettre aux collaborateurs de se connecter au réseau Wi-Fi ou VPN du bureau avec leurs identifiants Rippling et renforcez ainsi vos exigences d’authentification.
Chiffrez les appareils avec Filevault (macOS) et Bitlocker (Windows 10/11 Professionnel). Accédez aux clés de récupération détenues par l’autorité de séquestre directement dans Rippling, sur le profil de l’appareil.
Créez des rapports personnalisés et transformez-les en tableaux de bord pour obtenir facilement des informations sur votre parc d’appareils, leur statut et toute autre caractéristique d’intérêt. Aucun codage n’est nécessaire.
Installez automatiquement SentinelOne en quelques clics et gérez les menaces dans le système où vous gérez déjà vos appareils.
Suivez et installez les mises à jour du système d’exploitation pour Mac OS et Windows.
Instaurez des politiques de mot de passe personnalisées indiquant la longueur minimum, les types de caractères obligatoires, la complexité et la fréquence de rotation des mots de passe.
Réattribuez des appareils en cas de besoin, par exemple en attribuant à un collaborateur saisonnier l’ordinateur qu’il utilisait lors de sa précédente mission.
Verrouillez les ordinateurs ou effacez leur mémoire à tout moment et instantanément, où que vous soyez. Vous pouvez également planifier le verrouillage et l’effacement dans le cadre du processus d’offboarding des collaborateurs.
Gérez et sécurisez à distance vos ordinateurs Apple (ainsi que vos PC) avec notre logiciel MDM développé en interne. Tous vos ordinateurs sont accessibles au même endroit.
Gérez et sécurisez à distance vos ordinateurs Windows (ainsi que vos Mac) avec notre logiciel MDM développé en interne. Tous vos ordinateurs sont accessibles au même endroit.
Installez automatiquement les logiciels dont vos collaborateurs ont besoin en fonction de leur emploi (par exemple, service, échelon ou emplacement) afin qu’ils aient tout sous la main dès le premier jour.
Le déploiement MDM sans contact vous permet d’enregistrer les appareils de votre entreprise dans le système MDM de Rippling sans aucune intervention des utilisateurs.
Gestion des stocks
Expédiez en un seul clic un nouvel appareil entièrement configuré à vos collaborateurs, qu’ils aient récemment rejoint l’entreprise ou perdu ou endommagé un appareil. Comme nous avons le statut de revendeur agréé, vous pouvez acheter de nouveaux appareils directement dans Rippling. Et comme la plateforme repose sur une seule source commune d’informations, Rippling extrait automatiquement l’adresse de livraison du collaborateur tout en masquant ses informations personnelles pour toute personne qui ne devrait pas y avoir accès.
Rippling peut entreposer en toute sécurité vos appareils inutilisés. Tous les appareils font l’objet d’une inspection en 10 points, d’un effacement des données et d’un nettoyage physique. Avec un service d’entreposage sécurisé des appareils disponible aux États-Unis et dans plus de 26 autres pays, il s’agit de l’alternative la plus sûre à un entreposage dans une armoire informatique.
Envoyez automatiquement une boîte d’expédition avec emballage de protection et étiquette prépayée aux collaborateurs qui quittent l’entreprise pour qu’ils retournent leurs appareils, ce qui vous évite un déplacement jusqu’au relais UPS.
Rippling combine des fonctionnalités de sécurité professionnelles à des audits réguliers pour protéger vos données en permanence
Gérer vos appareils avec Rippling
Questions fréquentes
Qu’est-ce qu’un logiciel de gestion des appareils mobiles ?
Un logiciel de gestion des appareils mobiles (MDM) est une solution qui permet aux administrateurs et aux fournisseurs IT de gérer et de surveiller en toute sécurité les appareils mobiles, tels que les smartphones, les tablettes et les ordinateurs portables, à l’échelle d’une organisation. Cet outil permet aux entreprises d’appliquer des politiques de sécurité, de suivre l’utilisation des appareils, de déployer les mises à jour des applications et des logiciels, et de verrouiller ou effacer à distance les appareils en cas de perte ou de vol. Il garantit la protection des données de l’entreprise tout en assurant la conformité des appareils aux réglementations internes.
À quoi sert un logiciel MDM ?
Un logiciel MDM permet de gérer et de contrôler en toute sécurité les appareils mobiles au sein d’une organisation. Les solutions de gestion des appareils mobiles sont principalement utilisées pour :
- Appliquer des politiques de sécurité telles que le chiffrement, les exigences en matière de code d’accès et les restrictions.
- Gérer à distance les configurations des appareils, les mises à jour des logiciels et les paramètres en toute simplicité.
- Suivre et surveiller les appareils en cas de vol ou de perte et protéger les données de l’entreprise.
- Simplifier le provisionnement et le déprovisionnement des appareils tout au long du cycle de vie des collaborateurs (onboarding et offboarding).
- Garantir la conformité aux politiques de l’entreprise et aux normes réglementaires associées aux appareils mobiles et à la sécurité des données.
Comment bien choisir ma solution MDM ?
Choisir la bonne solution MDM dépend de divers facteurs propres aux besoins de votre organisation :
- Compatibilité des appareils : assurez-vous que la solution MDM prend en charge tous les types d’appareils que votre organisation utilise, tels que les appareils iOS, Android, Windows et macOS.
- Fonctions de sécurité : recherchez de solides fonctionnalités de sécurité telles que le chiffrement des données, l’effacement des données à distance, l’application des mots de passe et la possibilité de suivre et de localiser les appareils en cas de vol ou de perte.
- Évolutivité : optez pour une solution MDM capable d’évoluer avec votre entreprise. Assurez-vous qu’elle peut gérer le nombre d’appareils actuellement utilisés par votre organisation, et peut s’adapter facilement à l’intégration de nouveaux appareils et collaborateurs.
- Intégration avec les systèmes existants : choisissez une solution MDM qui s’intègre parfaitement avec votre infrastructure IT actuelle, telle que les outils RH, de gestion des logiciels ou d’autres outils de gestion des points de terminaison. Rippling, par exemple, intègre un logiciel MDM ainsi que des outils RH et de gestion IT. Regroupez l’onboarding, l’offboarding et la gestion des appareils dans une même interface.
- Facilité d’utilisation : déterminez si la solution est conviviale aussi bien pour les administrateurs que pour les utilisateurs finaux. Un logiciel offrant une expérience utilisateur intuitive et une console de gestion centralisée permet à votre équipe IT de déployer, surveiller et gérer facilement les appareils.
- Coût : établissez votre budget pour le logiciel MDM et évaluez le modèle de tarification. Certaines solutions MDM facturent en fonction du nombre d’appareils ou d’utilisateurs, tandis que d’autres proposent une tarification échelonnée reposant sur les options choisies. Assurez-vous que la tarification correspond aux fonctionnalités dont vous avez besoin.
Comment un logiciel MDM renforce-t-il la sécurité des appareils mobiles d’entreprise ?
Un logiciel MDM améliore la sécurité des appareils mobiles d’entreprise en proposant un éventail de fonctionnalités qui protègent les données sensibles, garantissent la conformité et évitent les accès non autorisés, notamment :
- Chiffrement des appareils : un logiciel MDM peut appliquer un chiffrement aux appareils, pour assurer que toutes les données stockées sur les appareils mobiles sont chiffrées de manière sécurisée, même en cas de perte ou de vol.
- Contrôle d’accès : la MDM permet aux organisations de contrôler la gestion des applications pour déterminer les services et applications accessibles sur les appareils mobiles.
- Application des politiques de sécurité : la MDM aide à appliquer les politiques de sécurité sur les appareils, concernant notamment la complexité des mots de passe, l’authentification à deux facteurs ou l’installation des correctifs de sécurité les plus récents.
- Gestion et surveillance des applications : avec la MDM, les équipes IT peuvent déployer, mettre à jour et supprimer des applications sur des appareils mobiles. Elles peuvent également suivre l’utilisation des applications pour s’assurer que seules les applications approuvées sont utilisées et que les applications malveillantes sont détectées et bloquées.
- Géorepérage et localisation : la MDM permet aux entreprises de suivre l’emplacement des appareils mobiles et de configurer un géorepérage afin de verrouiller ou d’effacer automatiquement un appareil s’il quitte les zones autorisées.
- Conformité et rapports : un logiciel MDM propose des fonctionnalités détaillées de rapport et d’audit pour garantir la conformité des appareils aux politiques de sécurité de l’entreprise et aux exigences réglementaires.
En centralisant la gestion, en appliquant des politiques de sécurité et en offrant des fonctions de surveillance à distance en temps réel, un logiciel MDM garantit que les appareils mobiles restent sécurisés, même lorsque les effectifs mobiles sont nombreux et éparpillés.
Qu’est-ce que le BYOD (Apportez votre propre appareil) ?
Le BYOD (Apportez votre propre appareil) désigne le fait d’autoriser les collaborateurs à utiliser leurs appareils personnels, tels que leurs smartphones, tablettes et ordinateurs portables, pour les tâches professionnelles. Le BYOD permet aux collaborateurs d’accéder aux ressources de l’entreprise, telles que la messagerie électronique, les applications et les fichiers, sur leurs propres appareils plutôt que de s’appuyer sur le matériel fourni par l’entreprise. Cette approche présente plusieurs avantages, tels qu’une plus grande flexibilité, des économies et une meilleure productivité, car les collaborateurs peuvent travailler de n’importe où et utiliser les appareils qui leur conviennent le mieux.