REPORTING
Gain total visibility into your users and devices in one place
Get the full picture of your devices and users, stay on top of security requirements, and prove SOC 2 compliance—all from one command center.
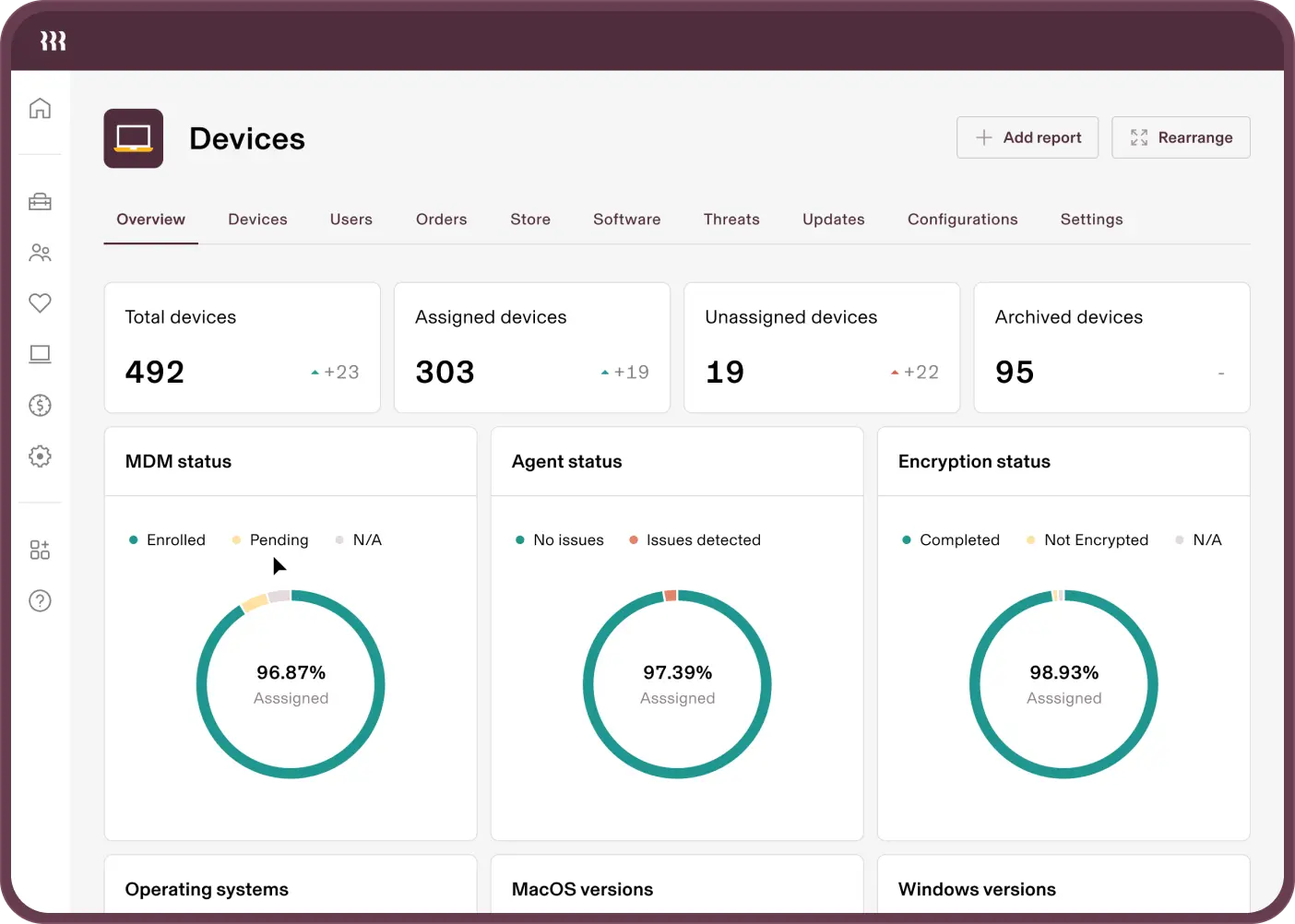
Centralized DATA
The source of truth for all user and device data
Quickly check the status of your security posture, users, and devices—all from one place. No more hopping between systems to piece together reports or audits.
Easily pull compliance evidence

Easily prove SOC 2 compliance in seconds. Take advantage of Rippling templates, or build your own custom reports combining any device or user attribute you want.
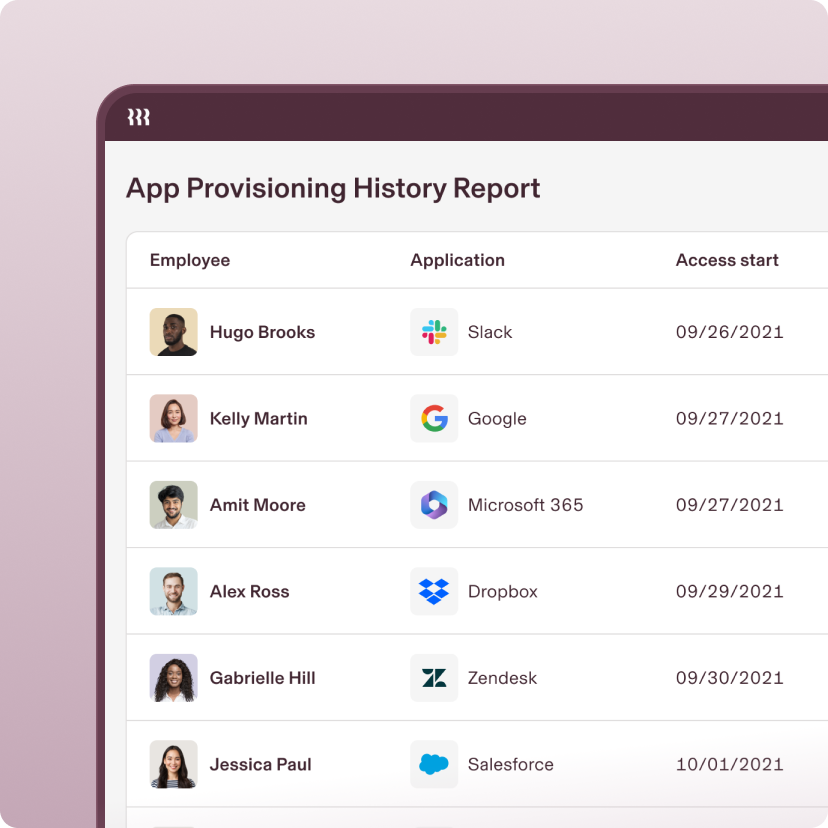
Monitor activity for security

Rippling’s data architecture seamlessly connects any data across HR and IT without manual exports, messy spreadsheet joins, or custom integrations.
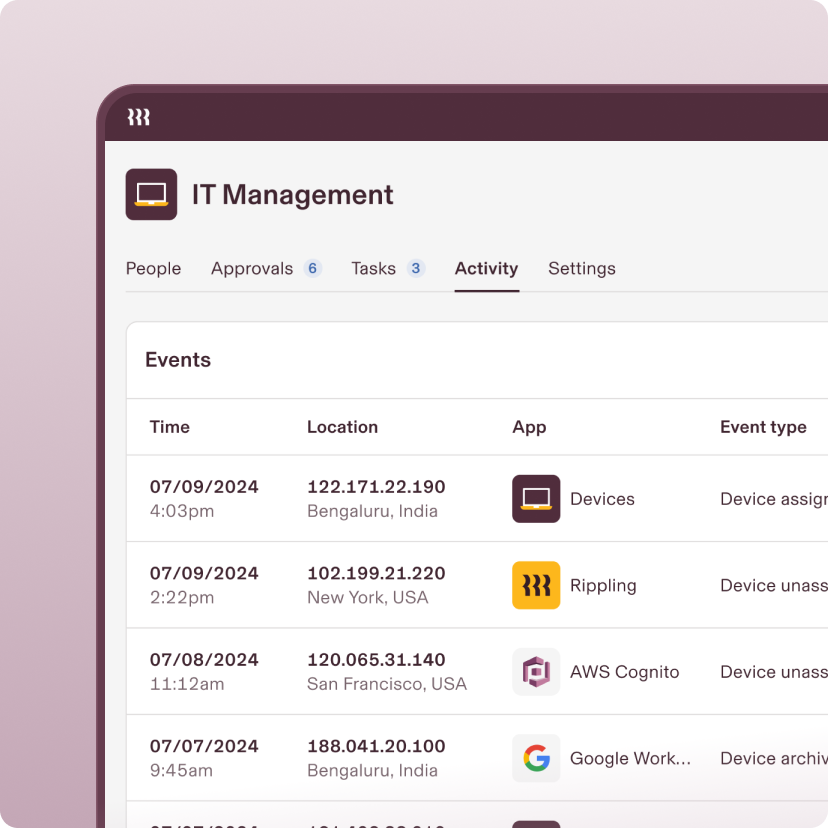
Customize reports

Rippling ensures you always have real-time access to the data you need. Drill deeper as needed with rich user and device attributes or complex calculations.
permissions
Empower leaders without sacrificing security
Automatically assign the appropriate level of access with role-based permissions.
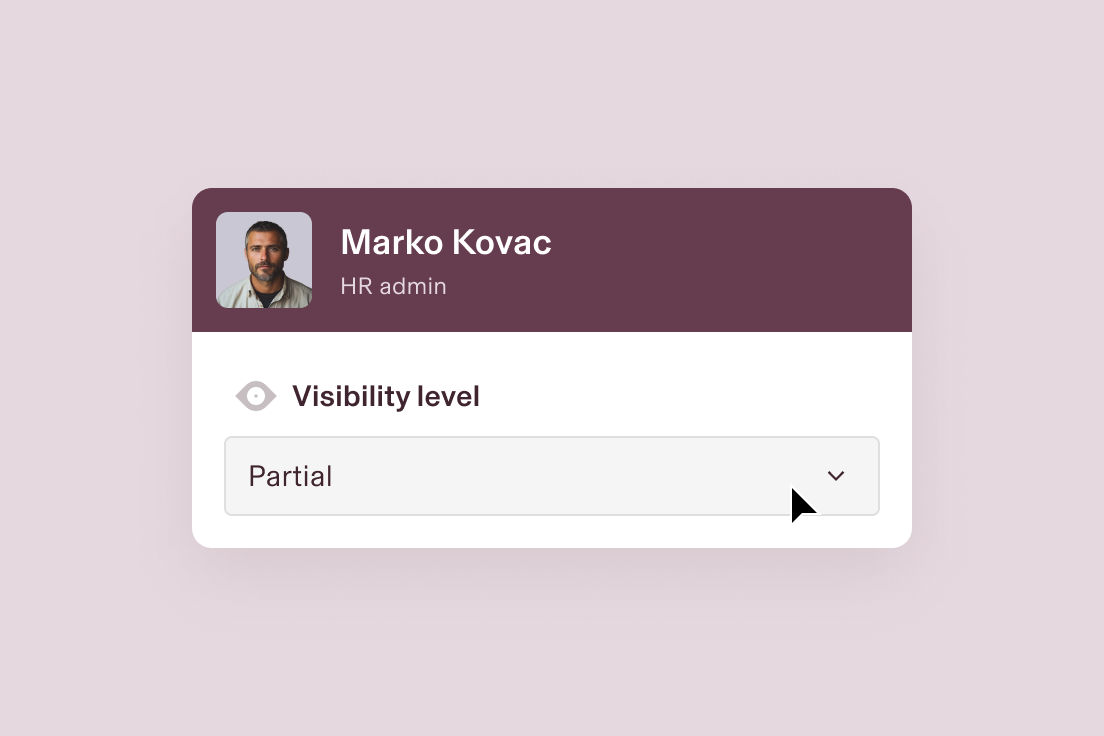
Set role-based permissions
If a user’s role changes, so too does their access. This ensures they have what they need while keeping data secure.
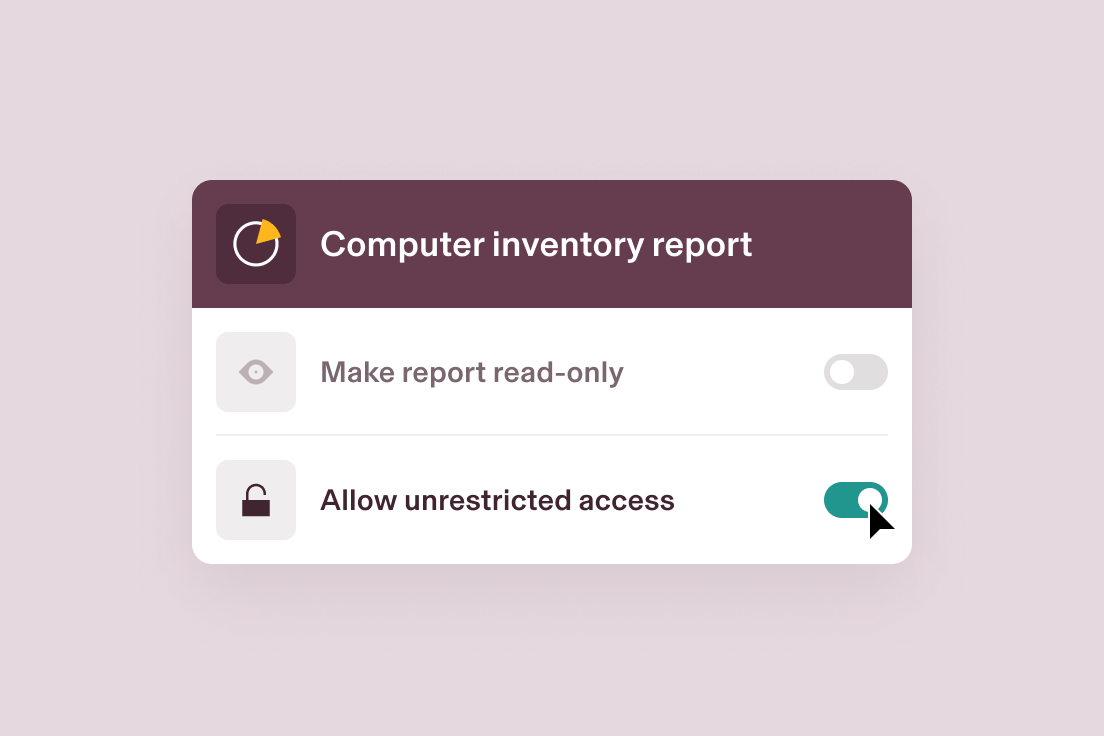
Specify access to reports
Rippling allows for flexible access so users can share reports based on role or choose to give viewers unrestricted access.
Reporting
Get more from your data with intuitive tools
Rippling’s point-and-click interface empowers you to create insightful reports from data across your entire organization.

Dynamic visuals
Choose from an array of visual display options like bubble charts, line graphs, scatter plots, and more.

Pivot tables
Summarize and analyze large amounts of data into an interactive table to better conduct analysis.

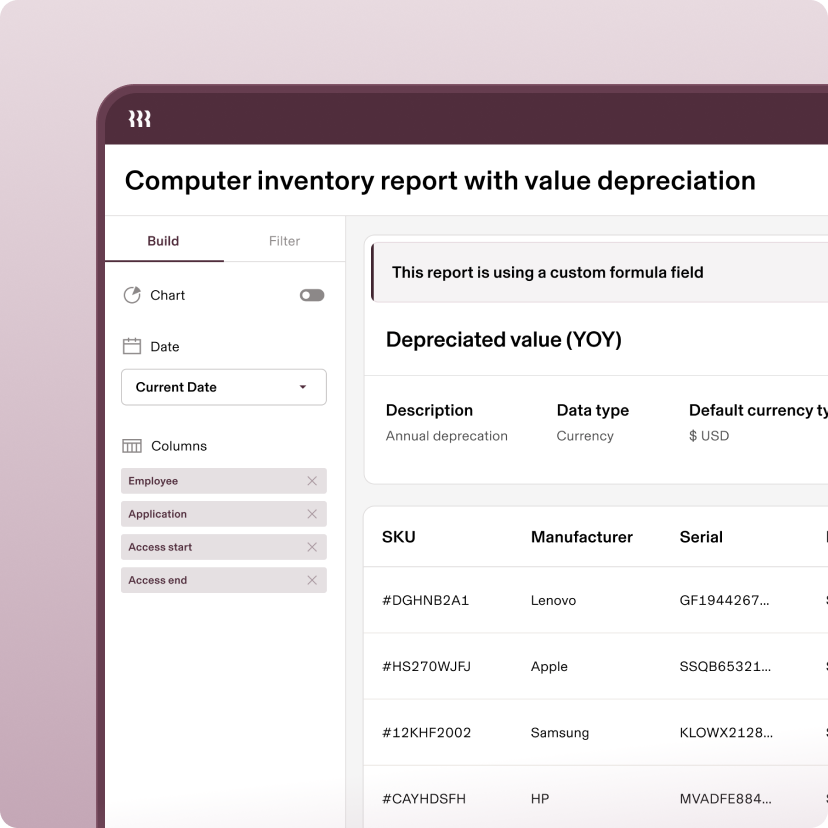
Formula fields
Automatically calculate a value based on other fields, records, or formulas to get more out of your data.
built different
The most efficient way to run IT
Take the effort out of IT with custom workflows, dynamic permissions and policies, and rich reports for users and devices.

Permissions
Automatically govern what each person in your company can see, do, and access.
Policies
Enforce your business’ unique rules with custom policies built on dynamic groups of users.
Workflows
Automate virtually anything with hyper-custom triggers and no-code workflows.
Analytics
Make better decisions faster with real-time, unified data in a report builder.
FAQs
What types of analysis are available out of the box?

Rippling offers several types of reports out of the box, including "joined reports" that allow users to create reports leveraging any field across any app, "custom reports" with flexibility to analyze almost any data tracked within Rippling, and "advanced reports" that consist of multiple data modules or report formulas.
How is data shared securely within Rippling?

Data within Rippling is shared securely by using access-controlled methods such as creating time-limited and access-controlled URL links, and using secure platforms like Jira, Salesforce, or Google Drive for sharing customer data. Additionally, Rippling emphasizes the importance of marking documents as "CONFIDENTIAL" and implementing access controls to ensure only those with a need-to-know can access sensitive information. Furthermore, Rippling has established a Data Perimeter project to secure data movement across all touchpoints, ensuring that only trusted identities access secure resources from specified networks.
Who can run reports?

In Rippling, the ability to run reports is generally available to employees who have been granted access through configurable field-level permissions. This allows a greater number of employees to "create workflows, run reports, etc." by increasing the proportion of employees with access to others' data in Rippling.

See Rippling IT in action
See how you can securely manage identity, access, devices, and inventory all from one platform




































































































