Policies
Enforce and automate security policies across your org
Easily create, deploy and enforce custom policies across apps and devices.
Trusted by 6,000+ customers










Supergroups
Apply policies to the right users automatically
Apply policies to users using Supergroups: dynamic membership lists that you can customise using attributes such as department, start date or security status. If an employee moves or changes roles, their policies are updated automatically.
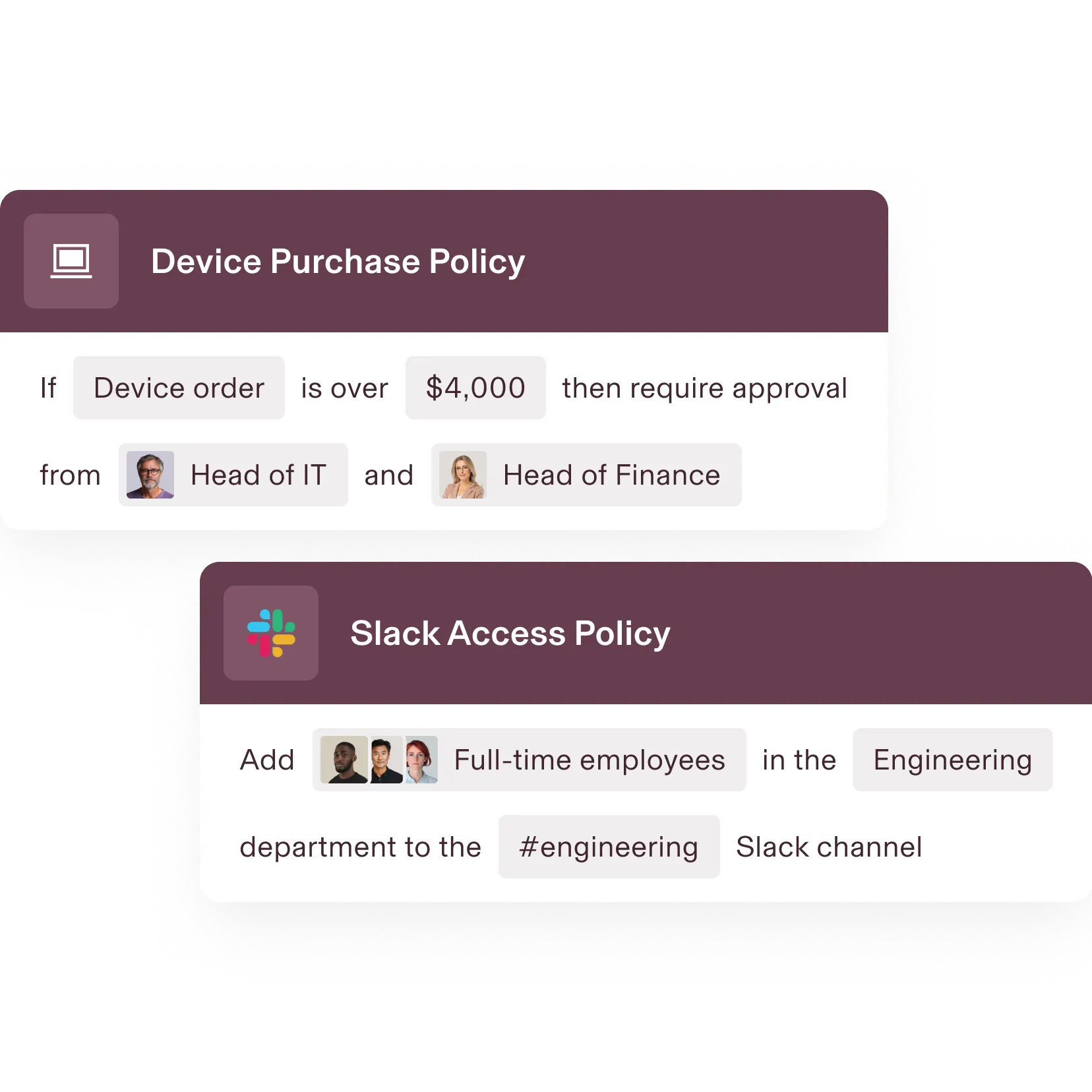
Policy CREATION
Customise policies to meet compliance needs
Rippling makes it easy to meet compliance and security requirements – applying your policies dynamically, so you never have to manually maintain who’s attached to each policy.
Access Policies

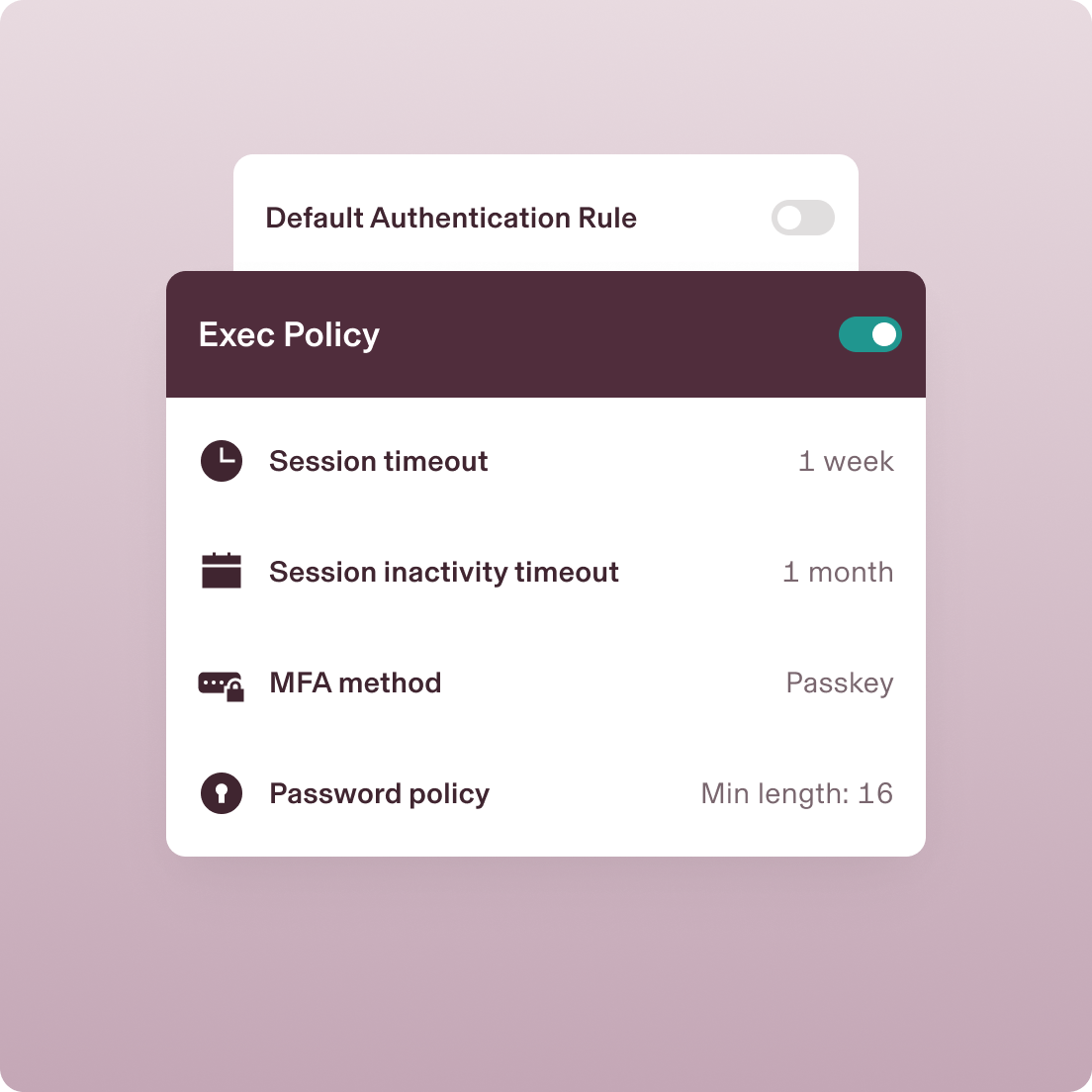
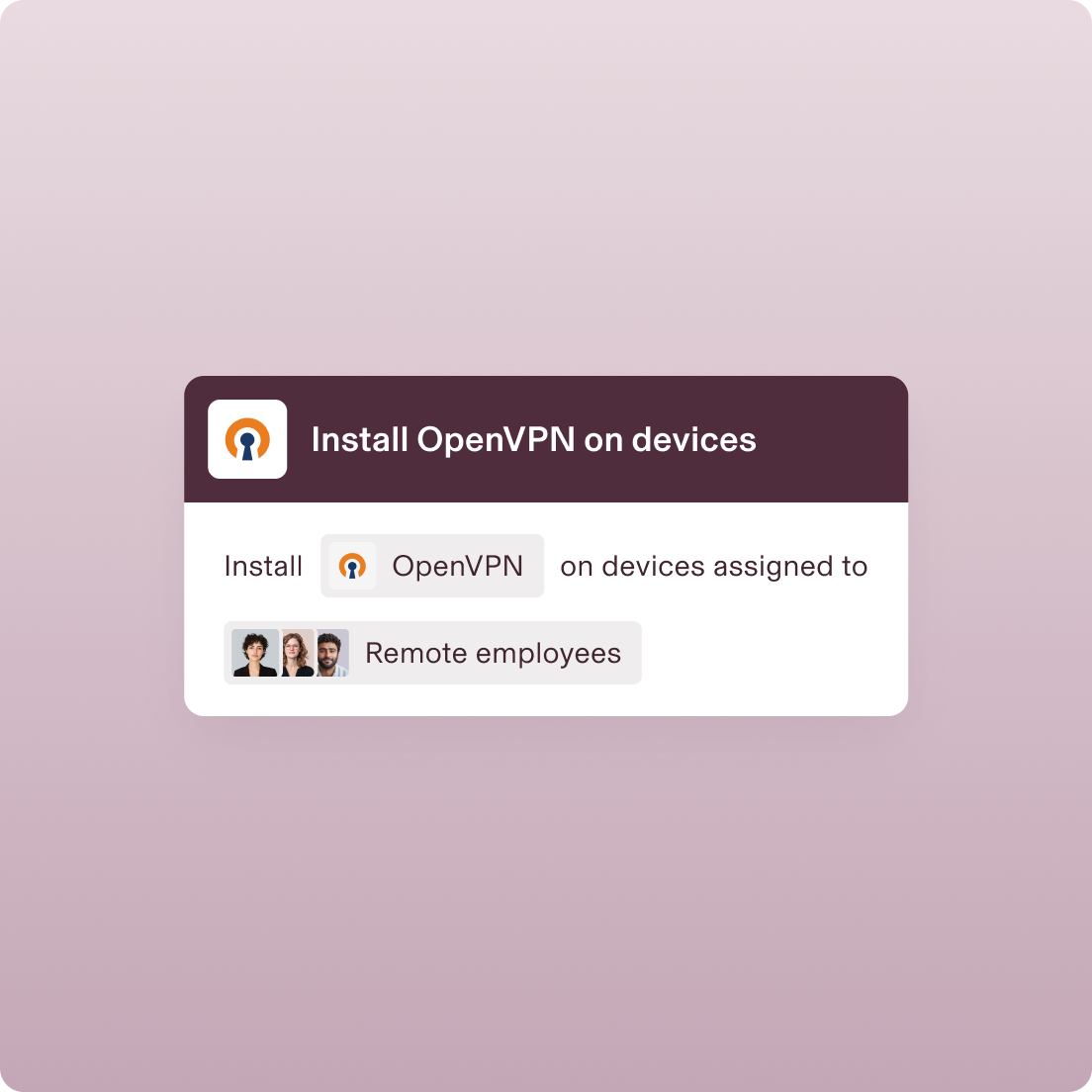
Device Policies

Zero-Trust Policies

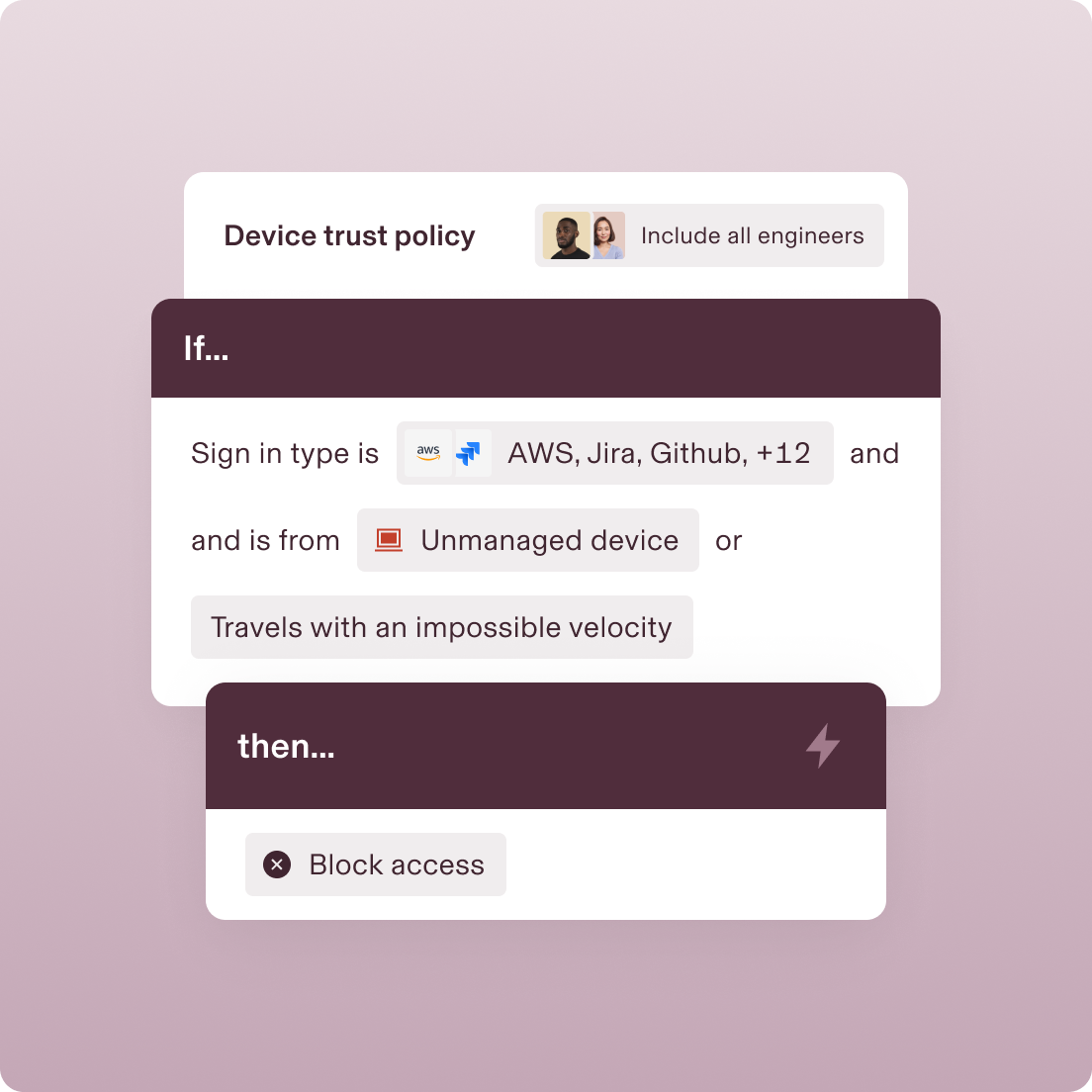
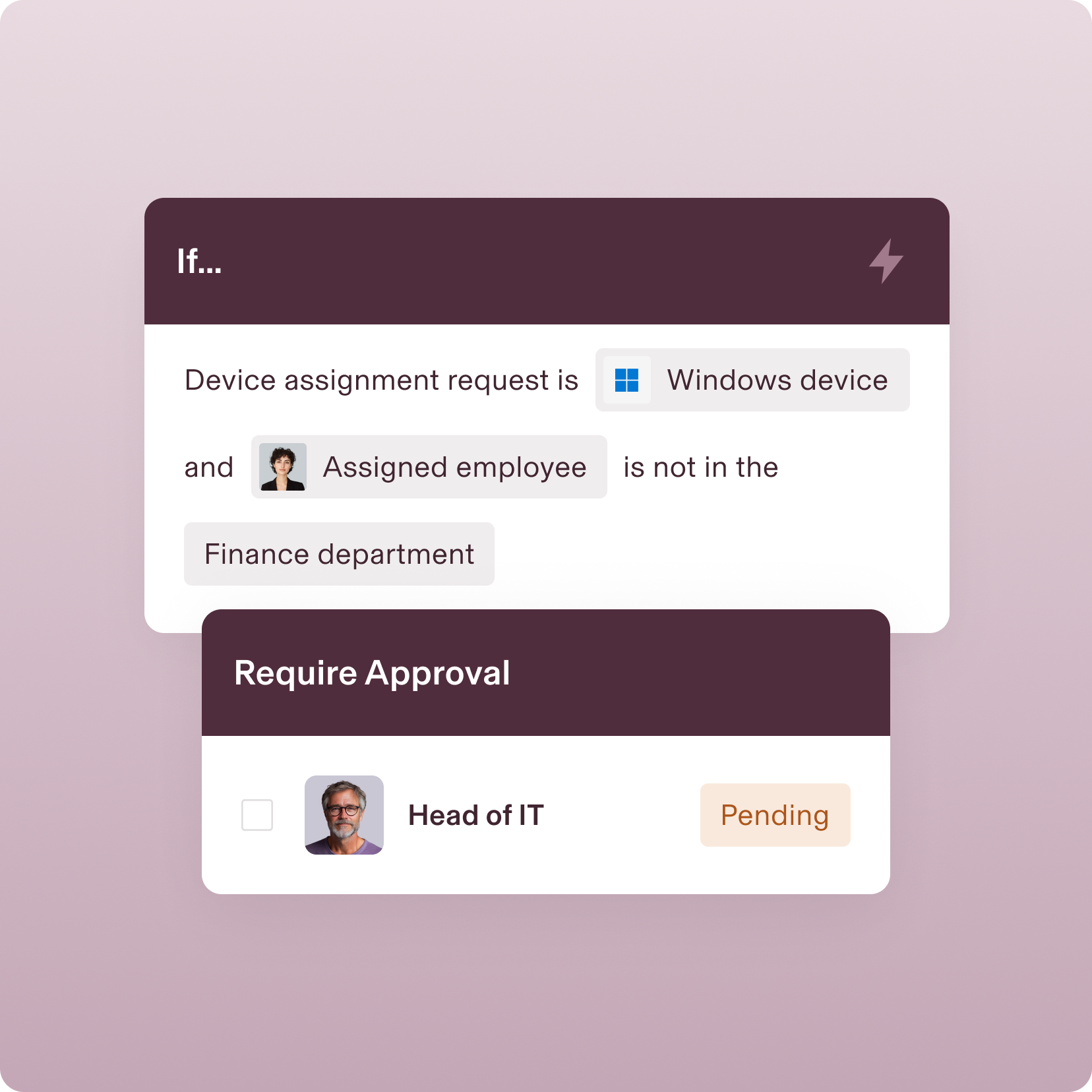
POLICY ENFORCEMENT
Customise policies based on any attribute
Ensure that nothing slips through the cracks with automated policy enforcement based on any possible attribute, such as device operating system, user role, location and more.
ROLE-BASED POLICY AUTOMATION
Update access when roles change – automatically
With Rippling, the correct policies are automatically applied when a user moves into a new role or Supergroup – no action needed from you.

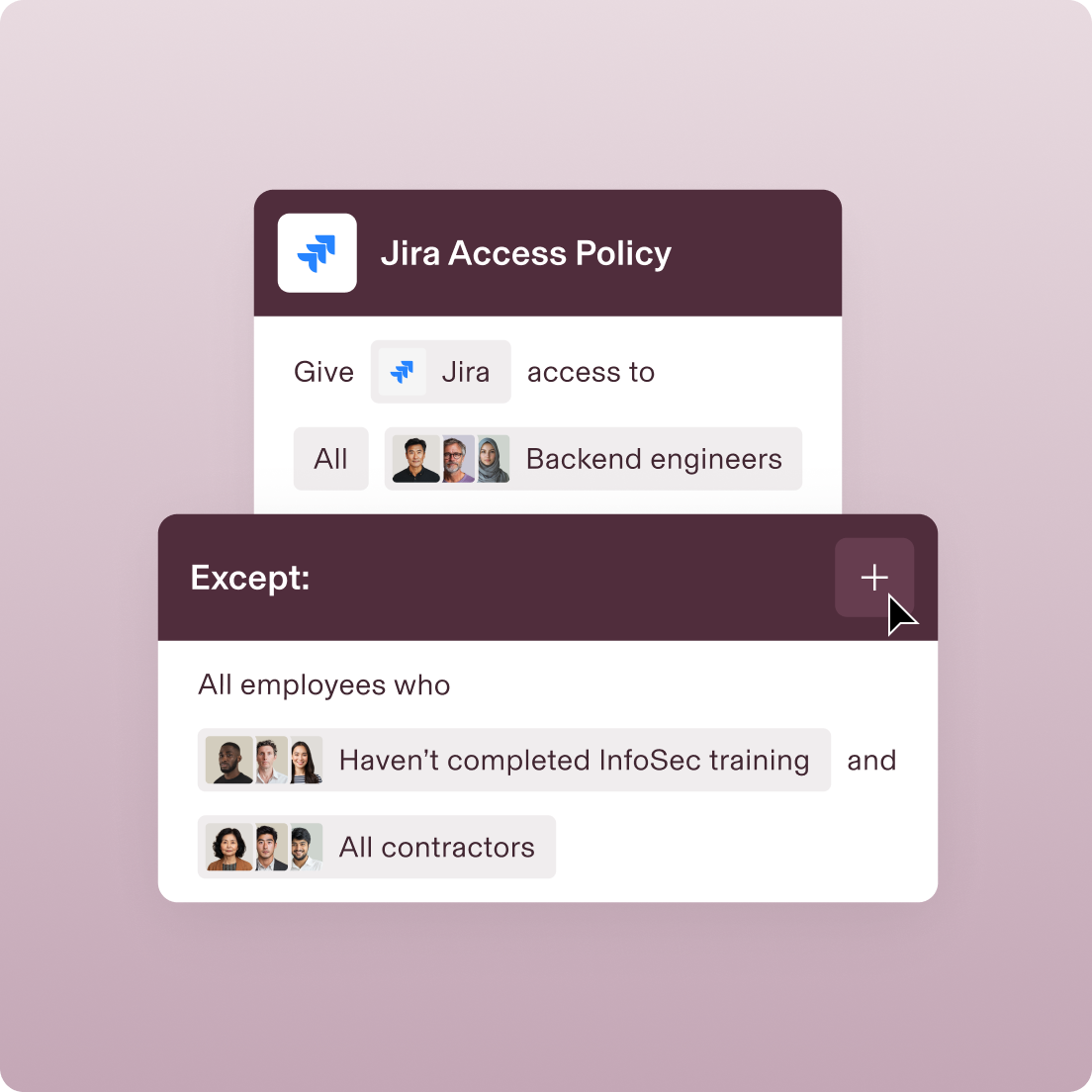
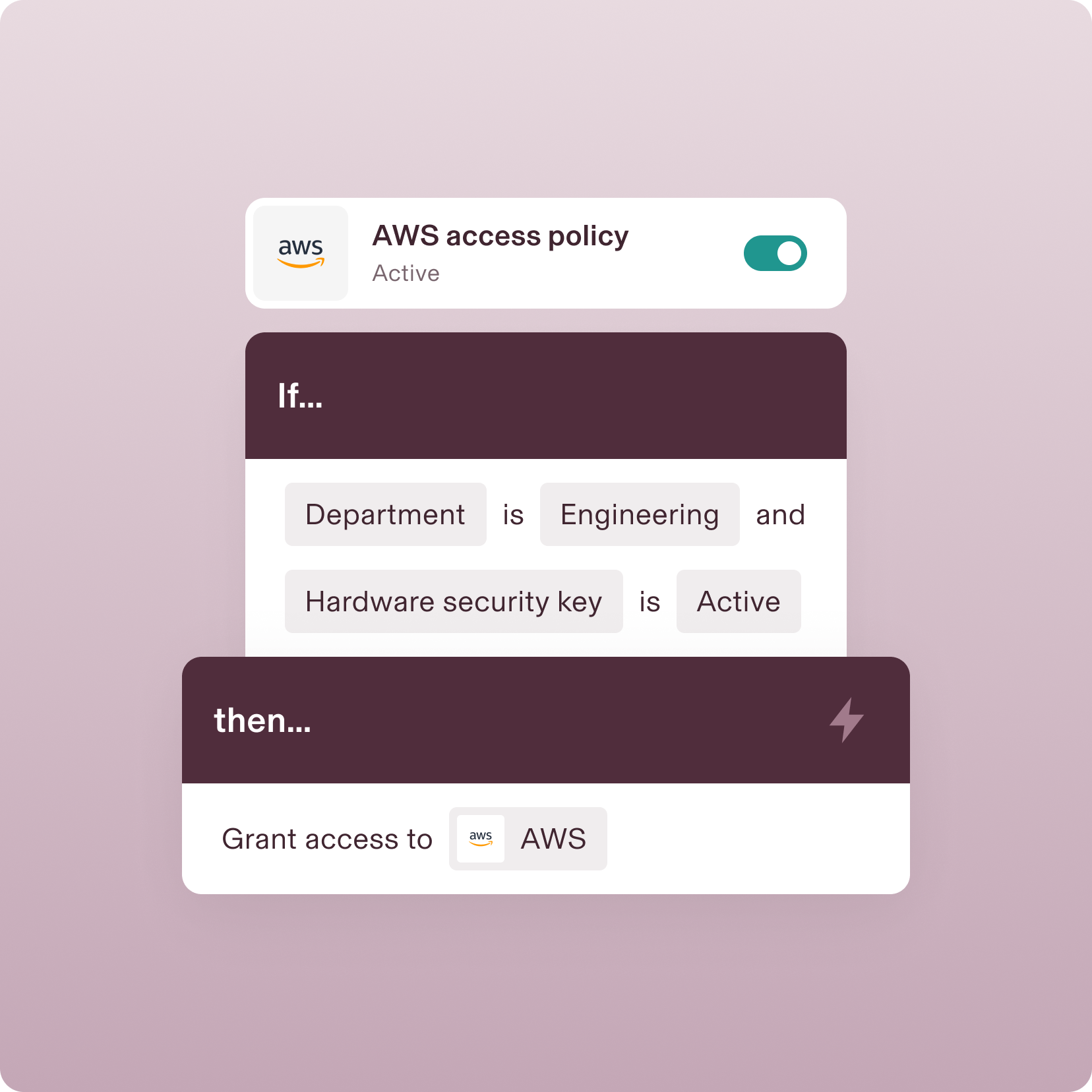
Cross-app policies
Create policies that span your tech stack
A policy triggered in one part of Rippling can enforce actions in another. For example, you can build a role-based access control that prevents engineers from getting Jira access if they haven’t completed their infosec training.
built different
The most efficient way to run IT
Take the effort out of IT with custom workflows, dynamic permissions and policies, and rich reports for users and devices.

Permissions
Automatically govern what each person in your company can see, do and access.
Policies
Enforce your business’ unique rules with custom policies built on dynamic groups of users.
Workflows
Automate virtually anything with hyper-custom triggers and no-code workflows.
Analytics
Make better decisions faster with real-time, unified data in a report builder.
FAQs
What is a policy?

A policy is a set of principles or rules that guide decisions and achieve rational outcomes. It is often documented and communicated to ensure compliance and understanding within an organisation. Policies can cover various areas such as information security, employee conduct and company procedures.
What is company policy enforcement?

Company policy enforcement refers to the implementation and regulation of specific rules or guidelines within an organisation to ensure compliance and maintain security. This can include enforcing authentication policies, such as Multi-Factor Authentication (MFA), especially for high-risk companies, to enhance security measures. It also involves managing and modifying authentication settings to align with company security policies.
Why are company policies important?

Company policies are important because they establish clear guidelines and standards for various processes, such as recruitment, ensuring fairness, transparency and efficiency. They also help in maintaining consistency and equity in practices, which is crucial for promoting a culture of excellence and career development. Additionally, policies serve as constraints or validations essential for determining eligibility for specific exemptions, streamlining processes and minimising efforts.
What are examples of a company policy?

Examples of company security policies include policies on the use of company devices, user registration and deregistration, access rights, external access, access reviews, password policy and user responsibilities. Other examples include policies on firewalls, anti-virus technology, spam filtering, software installation and scanning, vulnerability management, user awareness training and malware incident management. Additionally, there are policies for mobile device management, which involve implementing policies on device configuration, permitted software installation and remote actions such as device wiping.

See Rippling IT in action
See how you can securely manage identity, access, devices and inventory all from one platform





























































































































