Effortless identity and access management
Control access, automate user management, and enforce security without complexity.




One source of truth for user access
Centralize identity management with a global cloud-based user directory.

Automated onboarding & offboarding
Instantly provision and deprovision users across 600+ pre-built app integrations (plus custom SAML/SCIM support).

Zero trust protocols
Set up SSO, MFA, and granular access policies with just a few clicks.
Secure user access with a few clicks
SSO & App Access

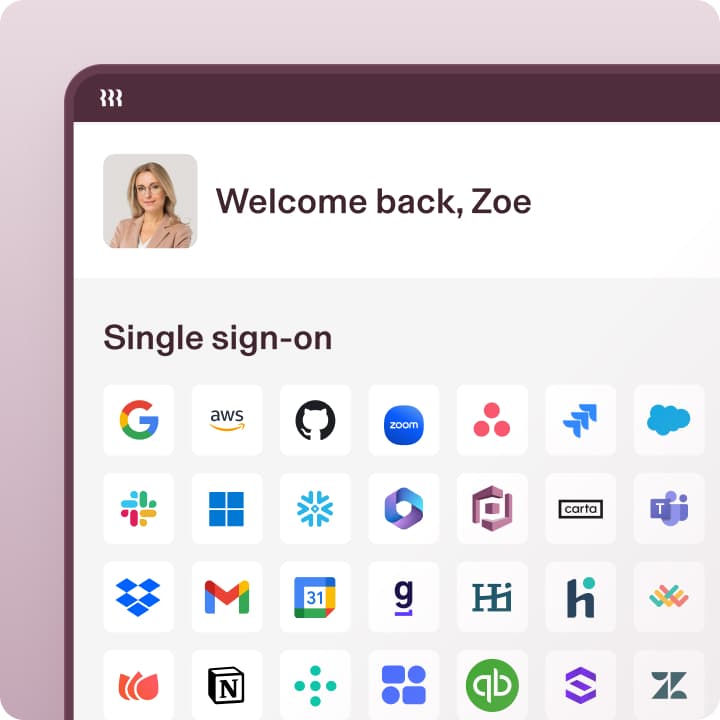
Provision access to 600+ apps
Skip the setup and give your team seamless access to Google, Microsoft, Jira, AWS, Slack, and more with pre-built integrations.
Store & share passwords in one place
Protect sensitive credentials with a zero-knowledge password manager, ensuring safe storage and effortless sharing.
Provide one-click access with SSO
Empower employees with a single sign-on (SSO) portal for fast, secure access to the tools they need.
Sync device & app passwords
Federate passwords by syncing credentials between devices and identity providers, or go passwordless with passkeys by enabling WebAuthn-based authentication
Automate access to 3rd-party groups
Automatically update group memberships in Google Groups (Organizational Units), Slack channels, and more without manual work.
Integrate any app with SAML/SCIM
Easily connect and provision users for any app with custom SAML/SCIM integrations—tailored authentication for your business.
Lifecycle Automation


Automate onboarding & offboarding
Use dynamic provisioning policies to instantly create, modify, or suspend user accounts based on real-time data changes.
Grant access automatically
Set up role-based (RBAC) and attribute-based (ABAC) access controls to automatically adjust app and license permissions based on role, department, location, or device.
Securely remove access
Instantly deprovision users or schedule access removal in advance to reduce security risks.
Simplify Google license management
Automatically purchase Google licenses as part of onboarding and transfer files, accounts, and calendar events during offboarding.
Streamline app requests & approvals
Centralize access requests from different departments and enforce custom approval chains with full visibility.
Create custom alerts & automations
Build custom workflows that trigger API calls or send notifications based on any action or data change.
Security Policies


Enforce multi-factor authentication (MFA)
Set role-based authentication policies with YubiKey, DUO, biometrics, or OTP, ensuring the right level of security for every situation.
Get SOC II compliant
View and export activities of users and apps to speed up compliance.
Prevent unauthorized access
Create conditional access policies to block or restrict logins based on real-time factors like location or impossible travel patterns.
Control app access by network & location
Set policies that allow or deny access based on IP address, VPN use, or specific geographic regions, protecting sensitive data from unauthorized locations.
Restrict access to trusted devices only
Ensure employees can only access company data from IT-approved and managed devices to prevent security breaches.
Identity Management


Unify HR & IT identities
Sync your HRIS with IT for a single, up-to-date cloud-based user directory with pre-built integrations for ADP, BambooHR, Gusto, Paylocity, and 50+ others.
Keep user data in sync
Automatically update attributes across all downstream systems.
Link identity across systems
Support seamless authentication with any protocol—LDAP, Active Directory, OIDC, RADIUS, SAML, and SCIM.
Auto-update user groups
Dynamically organize employees into groups based on attributes like department or location to keep access permissions updated.
Network access

Seamlessly connect apps with vLDAP
Automate user provisioning and secure authentication for LDAP-based applications—no manual configurations needed.
Secure network access with cloud RADIUS
Let employees use their Rippling credentials to authenticate across Wi-Fi and VPN networks, eliminating password management headaches.
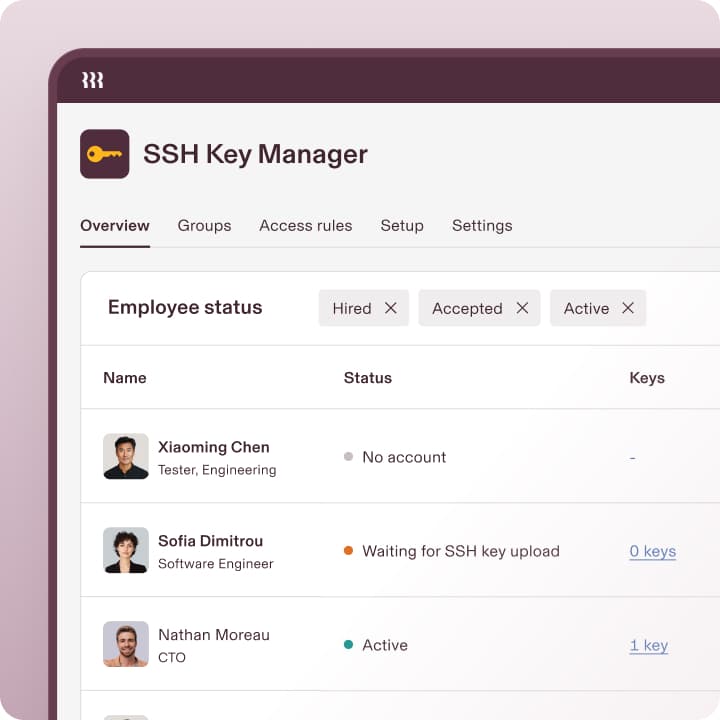
Automate SSH Key Management
Distribute just-in-time SSH keys based on user roles and automatically revoke access during offboarding to prevent security gaps.
Trusted by 6,000+ customers
















Frogslayer’s IT department onboards employees three times faster with Rippling
Employee downtime is lower because my technician is spending more time on tech support and less time on manual onboarding steps.”
Brian Cahill, Head of IT, Frogslayer
10
admin hours saved per month
3x
faster onboarding and offboarding with Rippling

IT Overview
All your IT tools in one place
Control the entire user lifecycle in one system with natively built identity, device, and inventory management tools, and 600+ integrations—including custom SCIM and SAML.
Identity & Access
Management
Identity & Access
Management
Device Management
Device
Management
Inventory Management
Inventory
Management




See Rippling IT in action
See how Rippling takes manual IT work off your plate — with all-in-one identity and access management, mobile device management, and inventory management.








